What is CTEM? Complete Guide to Continuous Threat Exposure Management
Gartner predicts that by 2026, organisations prioritising security investments based on a CTEM program will suffer two-thirds fewer breaches. Meanwhile, only 1% of published CVEs are actually exploited in the wild (VulnCheck, 2024), yet most security teams still chase every vulnerability equally.
This disconnect explains why traditional vulnerability management is failing. Continuous Threat Exposure Management, or CTEM, offers a different approach: focus on what attackers can actually exploit, not just what scanners find.
Get articles like this delivered to your inbox. Subscribe to CyberDesserts for practical security insights, no fluff.
What is CTEM?
CTEM stands for Continuous Threat Exposure Management. Gartner introduced the framework in 2022 as a systemic approach to continuously assess and prioritise security exposures based on real-world exploitability, not just theoretical risk scores.
The framework shifts security teams from reactive patch cycles to proactive exposure validation. Instead of treating every CVE equally, CTEM helps organisations understand which exposures actually matter to attackers targeting their specific environment.
At its core, CTEM answers a question most vulnerability programs cannot: "If an attacker targeted us today, which exposures would they actually exploit?"
Why CTEM Matters Now
Attack surfaces are expanding faster than security teams can track them. Gartner predicts that by 2026, non patchable attack surfaces will grow to include more than half of the enterprise. Shadow IT alone accounts for 30-40% of cloud usage in large enterprises (Gartner, 2024).
In 2024, 768 CVEs were reported as exploited in the wild, a 20% increase from 2023 (VulnCheck). Of these, 28.3% were exploited within one day of disclosure. Traditional patch cycles measured in weeks or months cannot keep pace.
Meanwhile, 69% of organisations admit they have experienced at least one cyber-attack that started by exploiting an unknown, unmanaged, or poorly managed internet-facing asset (ESG Research). You cannot protect what you do not know exists.
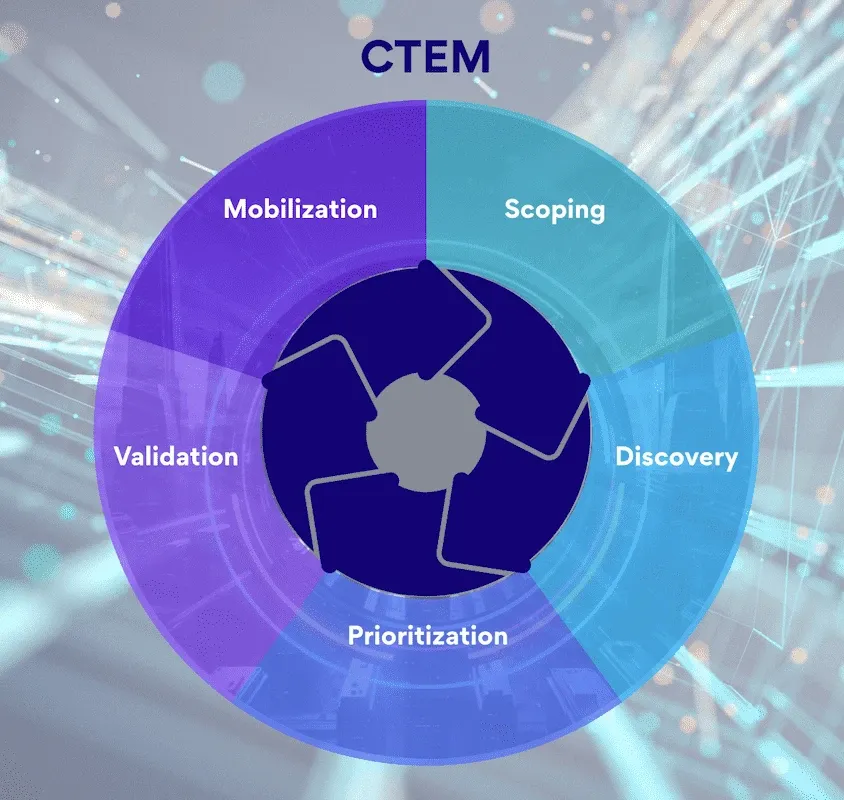
The 5 Stages of CTEM
Gartner's CTEM framework operates as a continuous cycle with five distinct stages. Each stage builds on the previous one, creating a feedback loop that improves over time.
| Stage | Purpose | Key Activities |
|---|---|---|
| 1. Scoping | Define what matters to the business | Identify crown jewels, critical assets, attack surfaces worth protecting |
| 2. Discovery | Find all assets and exposures | Asset inventory, shadow IT detection, vulnerability scanning, external attack surface mapping |
| 3. Prioritisation | Rank exposures by actual risk | Threat intelligence correlation, business impact analysis, exploitability assessment |
| 4. Validation | Test whether exposures can be exploited | Breach and attack simulation, penetration testing, red team exercises |
| 5. Mobilisation | Drive remediation across teams | Cross-team coordination, approval workflows, remediation tracking, executive reporting |
Stage 1: Scoping
Scoping defines the boundaries of your CTEM program. This is not about scanning everything. It is about identifying which assets, systems, and attack surfaces matter most to business operations.
Start with crown jewels: customer data, intellectual property, financial systems, and anything that would halt operations if compromised. Then map the attack surfaces that protect them.
Scoping also aligns security priorities with business risk tolerance. What the board cares about should drive what CTEM focuses on.
Stage 2: Discovery
Discovery identifies all assets and exposures within your defined scope. This goes far beyond traditional vulnerability scanning. It includes shadow IT, cloud resources, APIs, third-party integrations, and forgotten infrastructure.
Most organisations underestimate their attack surface. The goal is visibility into everything an attacker could target, whether IT knows about it or not.
Continuous discovery matters because environments change constantly. New cloud instances, API endpoints, and SaaS integrations appear daily.
Stage 3: Prioritisation
Prioritisation ranks exposures by actual exploitability and business impact, not just CVSS scores. This is where CTEM differs most from traditional vulnerability management.
Consider this: only 1% of published CVEs are exploited in the wild. Yet CVSS scores treat theoretical vulnerabilities the same as actively weaponised ones. CTEM incorporates threat intelligence to identify which exposures attackers are actually targeting.
Business context matters too. A medium-severity vulnerability on a system holding customer payment data may warrant faster action than a critical vulnerability on an isolated test server.
Stage 4: Validation
Validation tests whether prioritised exposures can actually be exploited in your environment. This is not theoretical, it involves controlled attack emulations.
Methods include automated security validation, breach and attack simulation (BAS), penetration testing, and red team exercises. The goal is to confirm that high-priority exposures are genuinely exploitable and that compensating controls work as expected.
Validation also tests remediation effectiveness. After fixes are applied, re-validation confirms the exposure is actually closed.
Stage 5: Mobilisation
Mobilisation drives remediation by reducing friction between security findings and operational fixes. Security teams can identify problems, but they rarely own the systems that need patching.
Effective mobilisation requires clear communication standards, documented approval workflows, and executive visibility into remediation progress. Without it, validated exposures sit unaddressed for months.
This stage also creates feedback loops. Lessons from remediation inform future scoping and prioritisation decisions.
CTEM vs Traditional Security Approaches
CTEM does not replace existing security tools. It provides a framework for using them more effectively. Understanding how CTEM relates to other approaches helps clarify where it fits.
| Approach | Focus | Limitation | CTEM Adds |
|---|---|---|---|
| Vulnerability Management | Finding CVEs | No exploitability context | Prioritisation and validation |
| Attack Surface Management | Asset discovery | Discovery without action | Scoping, validation, mobilisation |
| Penetration Testing | Point-in-time validation | Periodic, not continuous | Continuous cycle, business alignment |
| SIEM/SOC | Detection and response | Reactive to attacks | Proactive exposure reduction |
CTEM vs Vulnerability Management
Traditional vulnerability management finds CVEs. CTEM determines which ones attackers would actually exploit. The difference is prioritisation based on real-world threat intelligence rather than generic severity scores.
Vulnerability management remains essential for discovery. CTEM extends it with validation and business-aware prioritisation.
CTEM vs Attack Surface Management
Attack Surface Management (ASM) excels at discovery, particularly for external-facing assets. Many ASM capabilities map directly to CTEM's discovery stage.
CTEM extends ASM by adding the full cycle: scoping before discovery, prioritisation after it, and validation before mobilisation. ASM tells you what exists. CTEM tells you what to do about it.
CTEM vs SIEM
SIEM and SOC operations focus on detecting and responding to attacks in progress. This is reactive security: something bad happens, and you respond.
CTEM is proactive. It reduces exposures before attackers can exploit them. Both are necessary. CTEM findings can inform SIEM detection rules, while SIEM alerts can validate CTEM priorities.
For more on how CTEM integrates with detection capabilities, see our guide to SIEM selection for security teams.
Who Needs CTEM?
CTEM benefits any organisation with a complex attack surface, but the value increases with scale and regulatory exposure.
Large enterprises with sprawling infrastructure, multiple cloud providers, and extensive third-party integrations gain the most from CTEM's systematic approach. They often have vulnerability management programs that generate thousands of findings without clear prioritisation.
Regulated industries including finance, healthcare, and critical infrastructure face mounting compliance requirements that demand demonstrable risk reduction. CTEM provides the evidence trail that auditors want to see.
Organisations with mature security programs ready to move beyond checkbox compliance benefit from CTEM's outcome-focused approach. If your team is already running vulnerability scans and penetration tests, CTEM helps connect those activities into a coherent strategy.
Companies experiencing rapid digital transformation struggle to track expanding attack surfaces. Cloud adoption, API proliferation, and shadow IT create blind spots that CTEM's continuous discovery addresses.
Integrating CTEM with Existing Frameworks
CTEM does not replace governance frameworks like NIST CSF. It operationalises them. Where NIST tells you what outcomes to achieve, CTEM provides the continuous validation that those outcomes are actually working.
The alignment is natural. NIST's Identify function maps to CTEM's scoping and discovery. Protect maps to prioritisation and mobilisation. Detect and Respond improve when CTEM reduces the exposure surface that attackers can target.
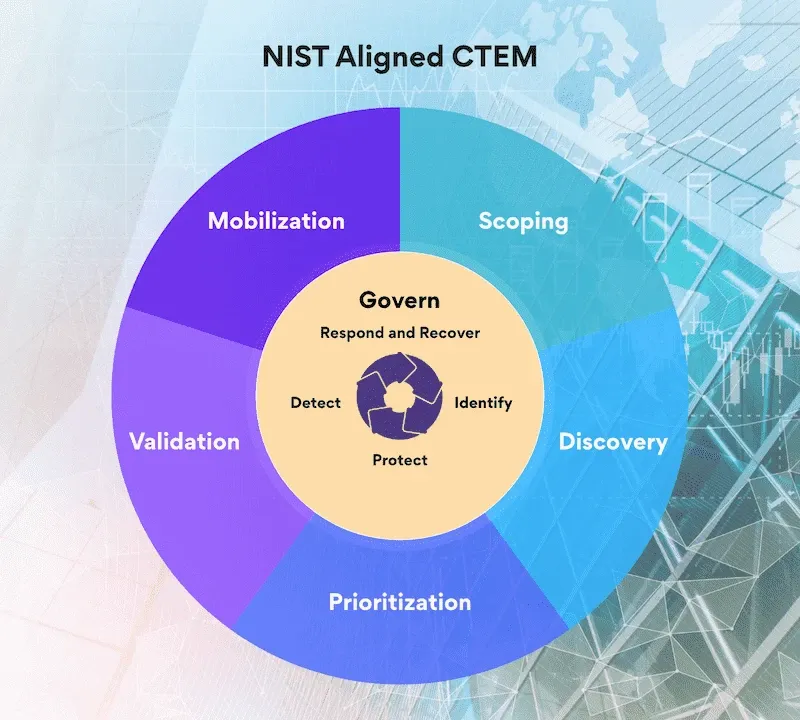
For a detailed breakdown of how CTEM enhances NIST implementation, see our guide to NIST-aligned CTEM.
Organisations building cybersecurity maturity models will find CTEM provides the operational discipline needed to progress from reactive tiers to adaptive, continuously improving security postures.
Getting Started with CTEM
Implementing CTEM does not require ripping out existing tools. It requires connecting them into a coherent process.
Start with scoping. Define the critical assets and attack surfaces that matter most. This is a business conversation, not just a technical exercise. Involve stakeholders who understand operational risk.
Audit your discovery capabilities. Can you identify shadow IT? Do you have visibility into cloud assets? External attack surface? Map gaps in your current asset inventory.
Evaluate prioritisation criteria. Are you using threat intelligence to identify actively exploited vulnerabilities? Do you incorporate business context into risk rankings? Most organisations rely too heavily on CVSS alone which is understandable based on a history of well known vulnerabilities that were weaponised to great effect.
Assess validation maturity. How often do you test whether vulnerabilities are actually exploitable? Annual penetration tests are insufficient for continuous threat exposure management.
Examine mobilisation effectiveness. How long does it take from validated finding to remediation? Where are the bottlenecks? Mobilisation failures undermine everything upstream.
Not sure where to start? Take our AI Security Maturity Assessment to identify your biggest gaps and get a customised improvement roadmap.
Summary
CTEM represents a fundamental shift from finding vulnerabilities to managing exposures. The distinction matters because attackers do not exploit CVE lists. They exploit specific weaknesses in specific environments.
Gartner's prediction of two-thirds fewer breaches for CTEM adopters is not magic. It reflects the compounding value of continuous prioritisation, validation, and remediation focused on what attackers actually target.
The framework integrates with existing security investments rather than replacing them. Vulnerability scanners, ASM tools, penetration testing, and SIEM all become more effective when connected through CTEM's five-stage cycle.
For organisations drowning in vulnerability data without clear action paths, CTEM provides the structure to focus effort where it matters most.
This guide gets updated as the CTEM landscape evolves. Subscribers receive notifications when major changes happen, plus weekly practical security content. No sales pitches, no fluff.
Frequently Asked Questions
What does CTEM stand for?
CTEM stands for Continuous Threat Exposure Management. Gartner introduced the framework in 2022 as a systematic approach to identifying, prioritising, validating, and remediating security exposures based on real-world exploitability rather than theoretical risk scores.
What are the 5 stages of CTEM?
The five stages of CTEM are: Scoping (defining critical assets and attack surfaces), Discovery (finding all assets and exposures), Prioritisation (ranking by actual exploitability and business impact), Validation (testing whether exposures can be exploited), and Mobilisation (driving remediation across teams).
What is the difference between CTEM and vulnerability management?
Vulnerability management focuses on finding CVEs through scanning. CTEM extends this by adding threat intelligence-based prioritisation, validation through attack simulation, and cross-team mobilisation for remediation. Only 1% of CVEs are exploited in the wild, so CTEM helps focus on exposures that actually matter.
What is the difference between CTEM and SIEM?
SIEM detects and responds to attacks in progress, which is reactive security. CTEM proactively reduces exposures before attackers can exploit them. Both are necessary and complementary. CTEM findings can inform SIEM detection rules, while SIEM alerts can validate CTEM priorities.
What is the difference between CTEM and attack surface management?
Attack Surface Management primarily covers discovery of external-facing assets. CTEM incorporates ASM capabilities within its discovery stage but extends the process with business-aligned scoping, threat intelligence-based prioritisation, validation testing, and remediation mobilisation.
Who created the CTEM framework?
Gartner introduced the CTEM framework in July 2022 through the report "Implement a Continuous Threat Exposure Management (CTEM) Program." The framework has since become a strategic technology trend, with Gartner predicting organisations prioritising CTEM will suffer two-thirds fewer breaches by 2026.
Last updated: December 2025
References and Sources
- Gartner. (2023). "Top Cybersecurity Trends for 2023." Prediction that CTEM adopters will suffer two-thirds fewer breaches by 2026.
- Gartner. (2025). "Cybersecurity Threats: Key Insights, Trends, and Best Practices." Prediction that nonpatchable attack surfaces will exceed half of enterprise by 2026.
- VulnCheck. (2025). "2024 Trends in Vulnerability Exploitation." Analysis showing 768 CVEs exploited in 2024, 20% increase from 2023, with only 1% of published CVEs exploited.
- VulnCheck. (2025). "Q1 2025 Exploitation Report." Finding that 28.3% of KEVs were exploited within one day of CVE disclosure.
- Gartner. (2024). "Shadow IT Statistics." Finding that shadow IT accounts for 30-40% of cloud usage in large enterprises.
- ESG Research. (2024). "Security Hygiene and Posture Management Report." Finding that 69% of organisations experienced attacks starting from unknown or unmanaged assets.
- Gartner. (2022). "Implement a Continuous Threat Exposure Management (CTEM) Program." Original framework introduction defining the five-stage CTEM cycle.

Member discussion