
Latest
01
Jan

When AI Writes the Code, Who Catches the Bugs?
In December 2025, Boris Cherny, creator of Anthropic's Claude Code, revealed he hadn't opened an IDE
6 min read
01
Jan

What is ClickFix? The Social Engineering Attack Bypassing Your Defences
ClickFix attacks surged 517% in the first half of 2025, now accounting for 8% of all blocked attacks (ESET, 2025)
6 min read
28
Dec

Hacktivist DDoS Attacks: A Defender's Guide
NoName057(16) has targeted 3,700+ hosts in thirteen months. Their playbook is predictable: strike during elections, holidays, and geopolitical flashpoints. Here's what the La Poste attack reveals about defending against hacktivist DDoS.
8 min read
27
Dec

14 Crypto Scams to Watch For in 2026
Cryptocurrency scam losses reached $9.3 billion in the United States alone in 2024, a 66% increase from the previous
20 min read
27
Dec

MongoBleed Exploit: The MongoDB Memory Leak Hitting 87,000 Servers
Updated December 30, 2025: Patched versions now visible in Shodan data, but adoption remains critically low - less than 6%
10 min read
22
Dec

Prompt Injection Attacks: Examples, Techniques, and Defence
Researchers tested 36 LLM-integrated applications and found 31 vulnerable to prompt injection. That is an 86% failure rate (HouYi Research,
13 min read
21
Dec

Building a Second Brain for Cybersecurity Work
Sixty-five percent of security professionals report their job has become harder in the past two years (ISSA/ESG, 2024). New
6 min read
16
Dec
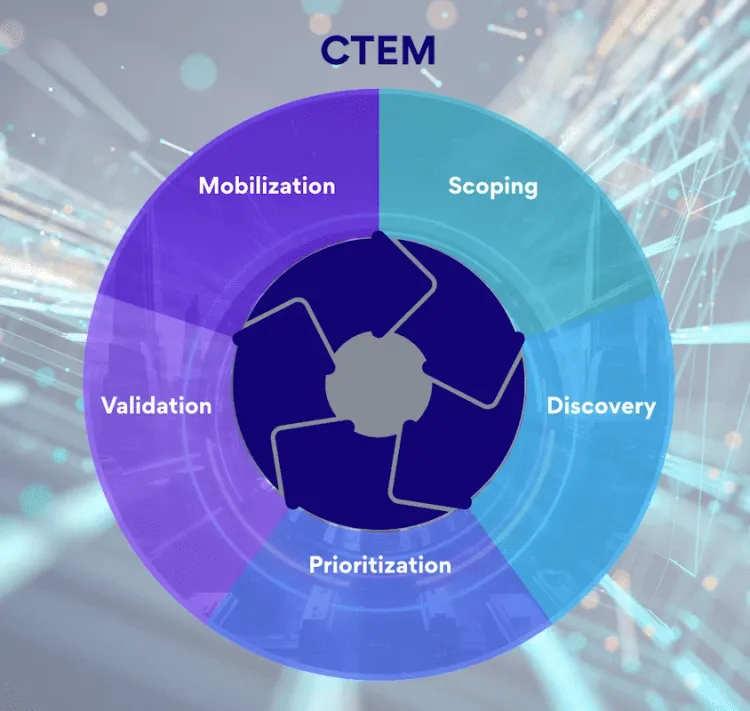
What is CTEM? Complete Guide to Continuous Threat Exposure Management
Gartner predicts that by 2026, organisations prioritising security investments based on a CTEM program will suffer two-thirds fewer breaches. Meanwhile,
9 min read
15
Dec

npm Security: The Complete Guide to Package Vulnerabilities
npm processes 4.5 trillion package requests annually, representing 70% year-over-year growth (Sonatype, 2024). This scale makes the JavaScript ecosystem
12 min read
14
Dec

Cybersecurity Career Path: Complete Guide for 2026
59% of organisations now report critical or significant cybersecurity skills gaps, up from 44% last year (ISC2, 2025). The narrative
11 min read

