10 Cybersecurity Best Practices That Prevent Breaches
Sixty percent of breaches still involve human actions (Verizon DBIR, 2025). Organisations know they should train employees, enforce MFA, and
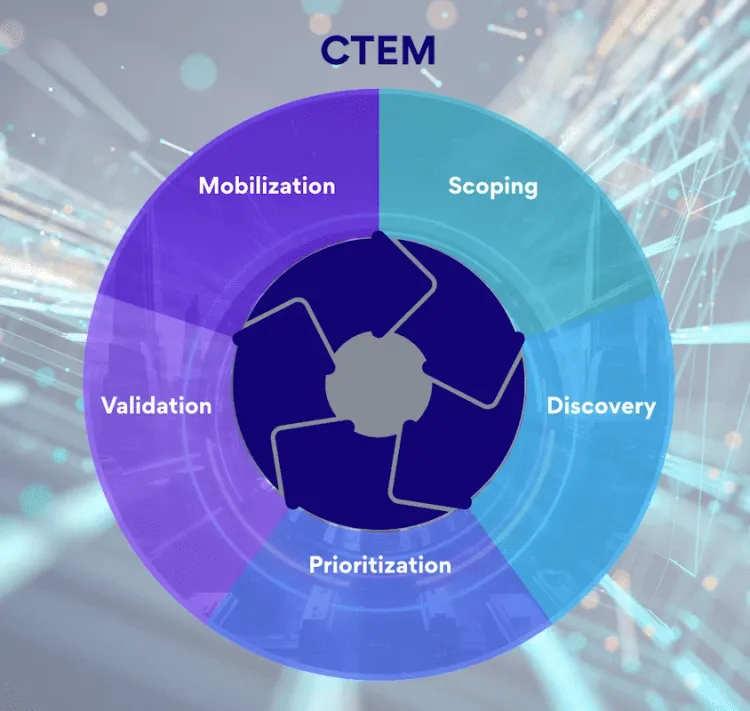
What is CTEM? Complete Guide to Continuous Threat Exposure Management
Gartner predicts that by 2026, organisations prioritising security investments based on a CTEM program will suffer two-thirds fewer breaches. Meanwhile,
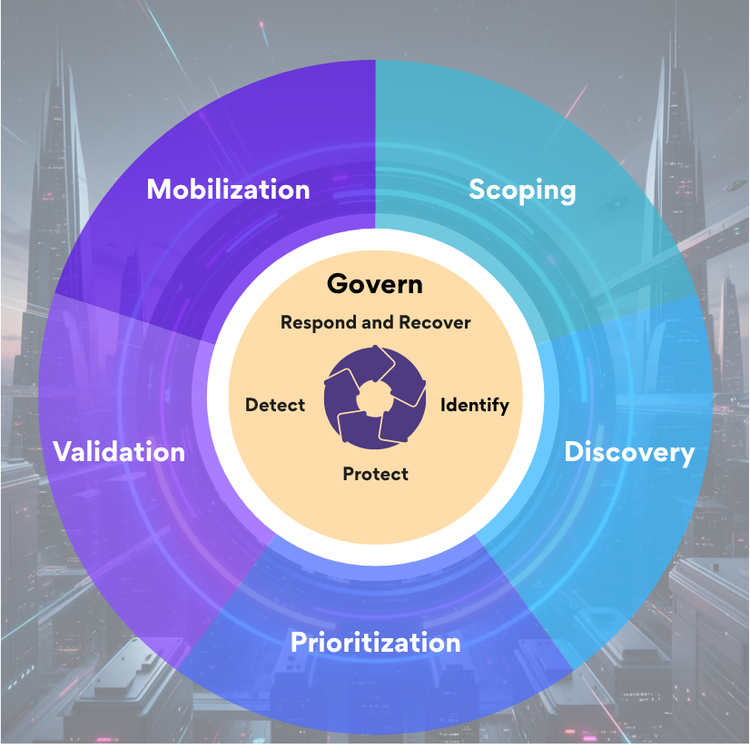
Why NIST Aligned CTEM Is the Framework Integration Security Teams Actually Need
TL;DR - Discover how NIST aligned CTEM transforms framework compliance into operational security. Bridge governance maturity and real threat detection through continuous validation of NIST CSF 2.0 controls.