Cybersecurity Skills Roadmap: Zero to Job-Ready

59% of cybersecurity teams report critical or significant skills gaps (ISC2, 2025). Entry-level positions have a 10% worker surplus, yet organisations struggle to find candidates with the right capabilities (Lightcast, 2024). The gap is not qualifications. It is practical skills and proof you can apply them. As a follow up to this article also check the best practices in cybersecurity.
56% of hiring managers say it takes 4-9 months to train entry-level hires to full productivity (ISC2, 2025). They want evidence you can learn, build, troubleshoot, and document your work.
This roadmap breaks the journey into four phases. Each builds on the previous one. This is also a discovery process where you will find what you like and what you don't like so much.
Subscribe to CyberDesserts for practical security content and free access to the AI assistant. You'll receive access within 24 hours of subscribing.
Choosing Your Cybersecurity Career Path
Cybersecurity is an ecosystem of specialisations: SOC analyst, penetration tester, GRC consultant, threat intelligence, incident response, cloud security, and more. The skills you prioritise depend on where you want to end up.
Research your target role before diving into random tutorials. Look at job postings for your target position. Note the required skills, tools mentioned, and typical career progressions.
The full guide maps out these tracks in detail. Over 30 pages focuses on building the skills once you have chosen your direction the guide covers project ideas , ai prompts , job readiness its all there based on my 20+ years of experience in the industry.



Download The Full Guide Packed With Career Advice - https://blog.cyberdesserts.com/cybersecurity-career-resources/
Using AI to Learn Cybersecurity Faster
AI tools have fundamentally changed how people learn technical skills. Used well, they compress months of struggle into weeks. Used poorly, they create a false sense of competence that collapses in interviews or on the job.
The practitioners who advance fastest treat AI as a sparring partner, not an answer machine. Try our very own learning assistant currently an experimental project.
What AI Does Well
Explaining concepts at your level. Struggling with subnetting? Ask AI to explain it three different ways, or use an analogy that connects to something you understand. Unlike static tutorials, AI adapts to your questions.
Diagnosing errors. Paste an error message with your code or command. AI excels at pattern-matching common problems and explaining what went wrong. This alone saves hours of frustrated searching.
Generating practice scenarios. Ask AI to create CTF-style challenges, quiz you on concepts, or generate realistic log samples for analysis. You can create unlimited practice material tailored to your level.
Translating between formats. Convert detection rules between SIEM platforms. Translate documentation from one tool to another. Reformat data for analysis.
What AI Does Poorly
Current information. AI training has cutoff dates. For recent CVEs, current tool versions, or emerging threats, verify against primary sources.
Replacing hands-on practice. Reading AI explanations of packet analysis is not the same as capturing and analysing packets yourself. Muscle memory comes from doing.
Guaranteeing accuracy. AI confidently produces plausible-sounding nonsense. It invents tool flags that don't exist, cites studies never published, and explains vulnerabilities incorrectly. This is routine, not occasional.
The Critical Thinking Rule
Question everything AI tells you. Verify commands before running them. Test explanations against documentation. If AI suggests a tool or technique, confirm it exists and works as described.
This is not a weakness. It is the skill you are developing. Security professionals must verify information, question assumptions, and validate claims. Practising this with AI output builds the exact mindset employers want.
When AI gives you an answer, ask yourself:
- Does this make sense given what I already know?
- Can I verify this against official documentation?
- What happens if I test this in my lab?
Prompting for Better Results
Vague questions get vague answers. Include your skill level, what you're trying to accomplish, what you've tried, and your specific environment.
Weak: "How do I use Nmap?"
Strong: "I'm scanning a lab network with three VMs. I want to identify all open ports and service versions on 192.168.1.0/24. What Nmap command should I use, and what does each flag do?"
The Responsibility Factor
AI can generate exploit code and attack scripts. Just because you can get this output doesn't mean you should use it carelessly.
In your lab: Experiment freely. Generate attack scenarios, test detection rules, explore techniques.
Against real targets: The same legal and ethical rules apply whether you wrote the code or AI generated it.
In your learning: Generating an answer is not understanding it. If AI writes a script for you, can you explain every line? Modify it? Debug it when it breaks? If not, you haven't learned.
Use AI to learn faster, debug quicker, and explore more widely, while building genuine understanding that holds up when the AI isn't available. Understanding AI capabilities also helps you recognise the threats surrounding AI security in your future self.
Check out this page if you want to see the latest on career trends, which skills and roles matter right now.
Download the 30-page pdf document that maps out the complete journey on how to get hired in cybersecurity covering skills , learning tracks, creating labs, ai prompts and interview prep.
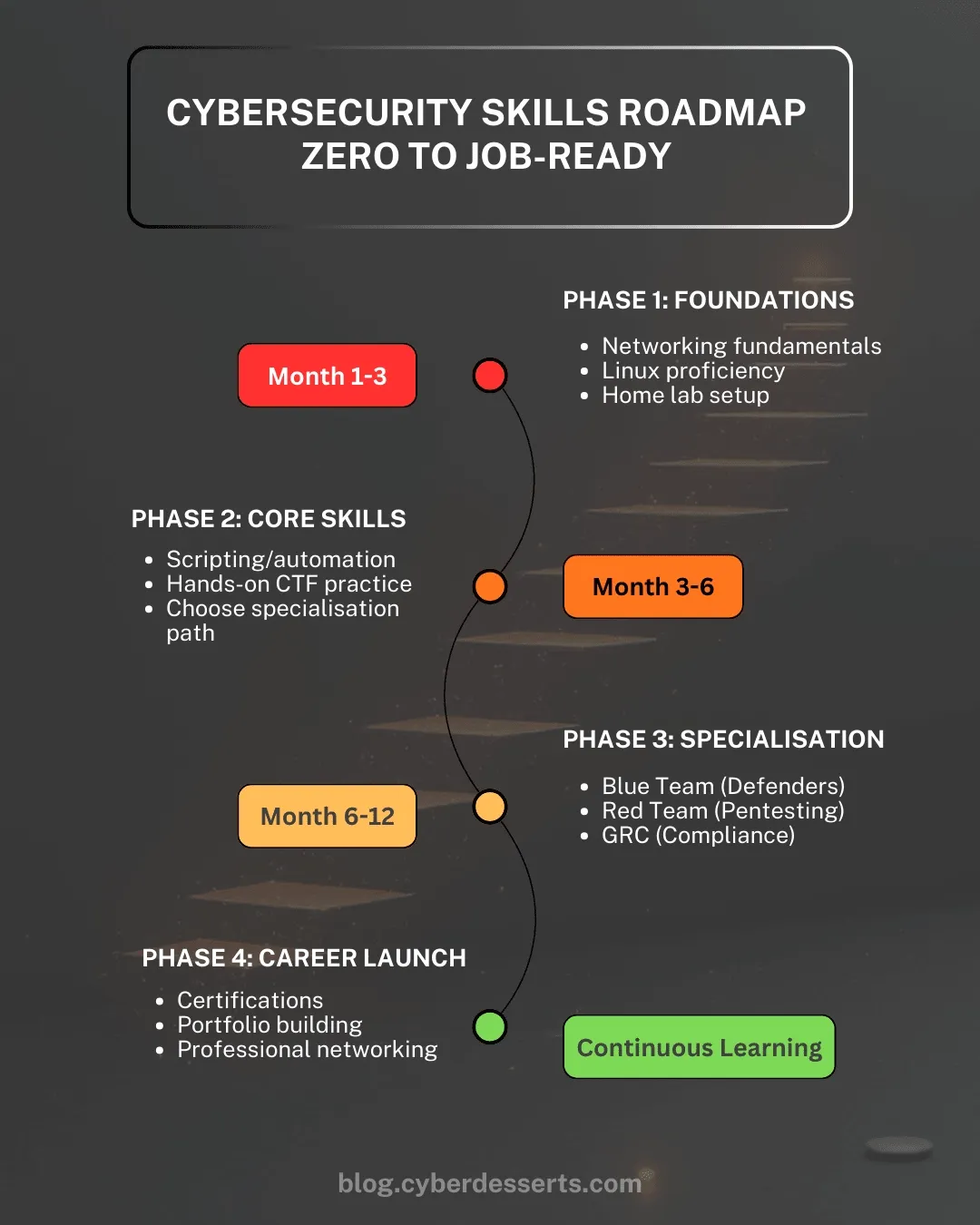
Phase 1: Essential Skills for Cybersecurity Beginners (Month 1-3)
The first three months establish the technical base everything else builds on. These skills apply regardless of specialisation. Let me stress you don't need to become an expert at this stage just start to get familiar and comfortable with foundational knowledge, expertise will come later.
Networking Fundamentals
You cannot defend or attack systems if you don't understand how they communicate.
Core concepts:
- TCP/IP protocol stack and how data moves across networks
- OSI model and where security controls operate at each layer
- DNS, DHCP, HTTP/HTTPS and common service protocols
- Subnetting, routing, and network architecture basics
Tools: Packet analysis with Wireshark. Network discovery with Nmap.
95% of security professionals use Nmap for network discovery (SANS Survey). The Nmap Scripting Engine guide covers automated vulnerability detection once you have the basics.
Linux Proficiency
96% of the world's top web servers run on Linux (W3Techs). You will use Linux daily in almost any security role.
Skills to develop:
- Command line navigation and file system operations
- User permissions, ownership, and access control
- Process management and system monitoring
- Log analysis and text processing (grep, awk, sed)
- Package management and system configuration
- Basic Bash scripting for automation
Start with Linux Basics for Hackers and follow the Linux for Cybersecurity learning path.
Setting Up a Cybersecurity Home Lab
A personal practice environment lets you learn without legal risk. Your lab is where you build real skills, this step already sets you apart and you will find your learning accelerates as you build and troubleshoot a home lab.
What you need to get started:
- VirtualBox or VMware (free for personal use)
- Kali Linux for security tooling
- Vulnerable targets: Metasploitable, DVWA, VulnHub machines
- Isolated network configuration
The Practice Lab Setup Guide walks through complete configuration. Docker for cybersecurity offers an alternative for spinning up environments quickly.
How to Document Your Cybersecurity Learning
Document every lab build, error message, and solution. This habit separates professionals from hobbyists.
Obsidian is a free, local-first note-taking tool that excels at connecting ideas. I have been using it for a few years and absolutely love it. Try it out, try a few out and see which app works for you. Use it to document commands, problems solved, and concepts learned. Link related notes together. See Building a Second Brain for Cybersecurity for ideas on how to push note taking to another level.
Phase 2: Building Core Security Skills (Month 3-6)
Phase 2 develops practical capabilities that make you useful on a security team. This is also when you choose your specialisation.
Scripting and Automation for Security
Security work involves repetitive tasks. Scripting multiplies your effectiveness.
Python focus areas:
- Reading and modifying existing security scripts
- Automating repetitive tasks
- Parsing logs and data files
- Interacting with APIs
- Building small tools that solve specific problems
You don't need to be a developer. You need to automate workflows and extend existing tools. This is also where AI tools like Claude code become a powerful co-pilot to understand, craft, and debug scripts.
Secondary scripting: Bash for Linux, PowerShell for Windows.
Hands-On Practice
CTF Platforms: Start with TryHackMe (guided rooms) or PicoCTF (beginner-focused). Progress to HackTheBox (realistic machines) and VulnHub (offline VMs). Document every challenge. Writeups become portfolio pieces.
Lab Progression: Build skills progressively in your home lab:
- Reconnaissance - Scan your lab network with Nmap. Identify services, versions, potential vulnerabilities.
- Traffic analysis - Capture packets with Wireshark while performing activities. Learn what normal and malicious traffic looks like.
- Log analysis - Enable logging on lab VMs. Correlate log events to actions manually before adding tooling.
- Detection - Deploy ELK Stack or Wazuh. Forward logs, build dashboards, create alerts.
- Attack and detect - Attack your own infrastructure, then find evidence of each phase in your logs.
The ELK Stack Security Monitoring Tutorial covers SIEM setup. Most entry-level jobs are defensive. Learning to catch attackers is as valuable as learning to emulate them.
Additional platforms: LetsDefend (SOC practice), CyberDefenders (DFIR challenges), PentesterLab (web app security).
Choosing Between Blue Team, Red Team, and GRC
By Month 6, choose your focus for the next 6-12 months:
Blue Team (Defensive): SOC analyst, threat hunter, incident responder. Focus on monitoring, detection, response.
Red Team (Offensive): Penetration tester, vulnerability researcher. Focus on finding and exploiting weaknesses.
GRC (Governance, Risk, Compliance): Compliance officer, risk manager, auditor. Focus on frameworks, policies, business risk.
Many practitioners move between tracks throughout careers. Choose a focus, not a permanent decision.
Phase 3: Specialisation and Advanced Skills (Month 6-12)
Phase 3 develops depth in your chosen track. These skills differentiate you from other candidates.
Blue Team Track
SIEM and Log Analysis: Master Splunk, ELK Stack, or Microsoft Sentinel. Write detection rules, correlate events, investigate alerts.
Threat Detection: Alert triage, IOC analysis, threat hunting, MITRE ATT&CK mapping.
Incident Response: IR procedures, evidence preservation, timeline reconstruction, reporting.
EDR: Understanding capabilities, alert investigation, endpoint forensics basics.
Red Team Track
Reconnaissance: Passive and active information gathering, service enumeration, attack surface mapping.
Web Application Security: OWASP Top 10, manual testing, Burp Suite, common exploitation.
Exploitation: Vulnerability validation, Metasploit, post-exploitation, privilege escalation.
Reporting: Clear, actionable vulnerability reports. This skill often determines who gets hired.
GRC Track
Frameworks: Deep familiarity with NIST CSF, ISO 27001, SOC 2, plus sector-specific (PCI-DSS, HIPAA). 27% of entry-level GRC postings prioritise framework knowledge over coding (Sprinto, 2025).
Risk Assessment: Risk identification, quantitative and qualitative methods, risk registers, communicating to stakeholders.
Policy and Compliance: Policy development, control mapping, audit preparation, vendor risk management.
In-Demand Cybersecurity Skills
The ISC2 2025 study identified critical gaps that will persist into 2026:
- AI Security (41% gap) - AI/ML vulnerabilities, prompt injection, model security
- Cloud Security (36% gap) - AWS, Azure, GCP security services. 94% of enterprises use cloud (Cloud Security Alliance)
- Risk Assessment (29% gap) - Quantifying and communicating risk to leadership
- Application Security (28% gap) - Secure coding, code review, DevSecOps
Target cloud fundamentals regardless of your track, the following article will also give you an idea on the changing threat landscape.
Soft Skills for Cybersecurity
Communication: Explain technical issues to non-technical audiences. Practice clear incident summaries.
Problem-solving under pressure: CTFs and complex lab scenarios build this muscle.
Phase 4: Getting Your First Cybersecurity Job
Technical skills open doors. Phase 4 converts capabilities into job offers.
Finding information independently is a core competency. The field moves too fast for any course to stay current.
Stay current: Follow threat intelligence feeds. Build RSS feeds and alerts for your speciality.
Experiment constantly: Most tools are free. Download them, break things in your lab.
Ask good questions: Demonstrate what you've tried before asking for help. The community helps those who help themselves.
Best Cybersecurity Certifications to Get First
Certifications prove baseline knowledge and pass HR filters. Choose based on track, target roles, and local market.
Industry Standard Certifications (Global Recognition)
| Track | Entry Level | Next Level | Certification Body |
|---|---|---|---|
| Foundation | CompTIA Security+ | CySA+ or cloud cert | CompTIA (est. 1982) |
| Blue Team | CompTIA CySA+ | GIAC GCIH, GCIA | CompTIA / SANS Institute |
| Red Team | eJPT | OSCP | INE / Offensive Security |
| Cloud | AWS Security Specialty, AZ-500 | CCSP | AWS, Microsoft, ISC2 |
| GRC | CISA, ISO 27001 Lead Implementer | CRISC, CISM, CISSP | ISACA (est. 1969), ISC2 |
About the Certification Bodies:
- ISC2 – Global nonprofit, 160,000+ members. CISSP is the gold standard for senior roles.
- ISACA – Established 1969, gold standard for audit/GRC with CISA, CRISC, CISM.
- SANS/GIAC – Premium certifications. Expensive but highly respected.
- Offensive Security – OSCP is the industry benchmark for penetration testing since 2006. Practical 24-hour exam.
- CompTIA – Vendor-neutral baseline. Security+ often the minimum for entry-level.
- INE – eJPT is a respected practical entry point for offensive security.
Practical Certifications (Hands-On Focus)
| Certification | Focus | Notes |
|---|---|---|
| OSCP | Penetration testing | 24-hour practical exam. Gold standard for offensive roles. |
| eJPT | Entry penetration testing | Practical format. Good stepping stone to OSCP. |
| GIAC certs | Various specialisations | Practical components. Premium pricing, highly respected. |
| CREST CRT/CCT | Penetration testing | Required for UK government testing. Recognised in UK, Australia, Asia. |
Emerging Practical Certifications
These are newer, gaining community traction, but may not be recognised by all HR departments:
| Certification | Provider | Notes |
|---|---|---|
| BTL1 | Security Blue Team | Launched ~2020. Excellent practical blue team content. Growing recognition. Good complement to CySA+. |
| PNPT | TCM Security | Well-respected founder. Includes report writing. May need explanation to some employers. |
Regional Considerations
- United Kingdom: NCSC Certified Training and CHECK for government work. CREST (CRT, CCT) for penetration testing.
- European Union: ISO 27001 certifications valued due to GDPR alignment. Privacy certifications (CIPP/E, CIPM) increasingly relevant.
- Germany: BSI certifications for government-adjacent work. ISO 27001 valued across industries.
- United States: Security+ meets DoD 8570/8140 for government and defence contractors.
- Australia/New Zealand: IRAP for government work. CREST and OSCP for offensive roles.
Framework-Specific Certifications
| Framework | Certifications |
|---|---|
| ISO 27001 | Lead Implementer, Lead Auditor (PECB, BSI, IRCA) |
| PCI-DSS | PCIP, QSA certification |
| Privacy/GDPR | CIPP/E, CIPM (IAPP) |
Building a Cybersecurity Portfolio
Your portfolio proves you can do the work.
GitHub: Scripts and tools, CTF writeups, lab configurations, detection rules.
Blog or documentation: Technical tutorials, project documentation, challenge writeups.
Include: Home lab architecture, CTF solutions with methodology, tools built or modified, detection rules created.
Professional Networking for Cybersecurity
Most jobs aren't posted publicly. Referrals bypass HR filters.
Organisations: ISC2, ISACA, ISSA (all have local chapters with events).
Events: BSides conferences (community-organised, accessible), local meetups, OWASP chapters.
Online: LinkedIn engagement, Discord communities (TryHackMe, HackTheBox).
Give before you ask. Share resources, answer questions, help others.
How to Get Into Cybersecurity With No Experience
Don't force a jump to "security analyst" from zero.
IT roles as stepping stones: Helpdesk, network admin, support engineer build paid experience while you develop security skills.
I started on frontline helpdesk, resolving tickets daily. That foundation made everything that followed easier.
The vendor backdoor: Solutions Engineer or Customer Success at security vendors provides access to enterprise tools and training. If direct security roles aren't opening, vendor-side offers an alternative path.
This is just the beginning download the full 30-page pdf guide that maps out the complete journey on how to get hired in cybersecurity covering skills , learning tracks, creating labs, ai prompts, interview prep and much more.
Frequently Asked Questions
How long does it take to learn cybersecurity?
With focused effort, you can be job-ready in 12 months. The first three months build foundations (networking, Linux, lab setup). Months 3-6 develop core skills. Months 6-12 focus on specialisation. Some people move faster, some slower. Consistency matters more than speed.
Do I need a degree for cybersecurity?
No. While degrees help for some roles and employers, most hiring managers prioritise demonstrable skills, certifications, and practical experience. Your home lab, CTF writeups, and portfolio often carry more weight than academic credentials. That said, degrees can help with visa sponsorship and some government roles.
What cybersecurity certification should I get first?
CompTIA Security+ is the most common starting point. It provides a vendor-neutral baseline that most employers recognise. After that, choose based on your track: CySA+ or BTL1 for blue team, eJPT for red team, or CISA for GRC.
Can I learn cybersecurity with no IT background?
Yes, but expect to spend extra time on Phase 1 foundations. Networking and Linux fundamentals may take longer without prior exposure. Many successful security professionals came from non-technical backgrounds. The key is building hands-on skills through labs and practice, not just reading about concepts.
What is the best cybersecurity career path for beginners?
SOC Analyst is the most common entry point. These roles have the highest volume of openings and typically require Security+ plus demonstrable skills. From there, you can specialise into threat hunting, incident response, or pivot to offensive security or GRC based on your interests.
How much do entry-level cybersecurity jobs pay?
Salaries vary significantly by region. In the UK, entry-level SOC analysts typically earn £25,000-£35,000. In the US, $50,000-$70,000 is common for entry-level roles. Higher cost-of-living areas and specialised skills command higher salaries. Remote work has expanded options but also increased competition.
Should I learn programming for cybersecurity?
You don't need to be a software developer, but scripting ability is essential. Python is the most useful language for security work. Focus on reading and modifying existing scripts, automating tasks, and parsing data. Full application development skills are only necessary for specific roles like application security or tool development. Important note, AI is now good enough to code you bring the thinking and clarity on what you want to achieve when prompting.
Is cybersecurity a good career in 2026?
The skills gap continues to widen. The ISC2 2025 study found 59% of organisations report critical skills shortages, and this trend is expected to continue. Demand spans every industry. The challenge is breaking in initially, which this roadmap addresses. Once established, career options are extensive.
Your 12-Month Action Plan
Phase 1 (Month 1-3): Foundations
Set up home lab and knowledge base. Master networking fundamentals and Linux. Learn Nmap and Wireshark. Join one security community. Learn about threat actor tradecraft.
Phase 2 (Month 3-6): Core Skills
Develop Python scripting. Complete 20+ CTF challenges. Build SIEM in your lab. Choose specialisation track.
Phase 3 (Month 6-12): Specialisation
Deep dive into track-specific skills. Build portfolio projects. Add cloud security fundamentals. Start certification preparation.
Phase 4 (Month 12+): Career Launch
Complete certification. Publish portfolio. Activate professional network. Apply strategically.
For the 18 skills that separate top performers, see the Cybersecurity Career Playbook.
This roadmap gets updated as the skills landscape shifts. Subscribers receive notifications when major changes happen, plus weekly practical security content.
Last updated: January 2026
References and Sources
- ISC2. (2025). 2025 Cybersecurity Workforce Study. Survey of 16,029 professionals. 59% report critical skills gaps. 56% of hiring managers say 4-9 months to train entry-level hires.
- Lightcast. (2024). Quarterly Cybersecurity Talent Report Q3 2024. Entry-level positions show 10% worker surplus.
- W3Techs. (2025). Web Server Usage Statistics. 96% of top web servers run Linux.
- SANS Institute. (2024). Security Tool Usage Survey. 95% of professionals use Nmap.
- Cloud Security Alliance. (2024). State of Cloud Security Report. 94% of enterprises use cloud services.
- Sprinto. (2025). GRC Cybersecurity Career Roadmap. 27% of entry-level GRC postings prioritise framework knowledge.





Member discussion