Cybersecurity Best Practices: Closing the Gap Between Knowing and Doing

Sixty percent of breaches still involve human actions (Verizon DBIR, 2025). This statistic has barely moved in years. Organisations know they should train employees, enforce MFA, and patch systems. Most have policies that say exactly that.
The problem is not knowledge. The disconnect is between knowing what to do and investing the time to implement it consistently when budgets are tight and business demands are loud.
This guide focuses on why implementation fails and how to fix it not just looking at cybersecurity best practices but addressing actual problems faced by organisations.
Get practical security insights delivered weekly. Subscribe to CyberDesserts for threat intelligence and implementation guidance. No vendor pitches.
Table of Contents
- Why Cybersecurity Best Practices Fail
- Cybersecurity Measures and Best Practices That Work
- Building Detection and Response Capability
- Securing the Supply Chain
- How AI Is Reshaping Security Practice
- Building Security Culture for Employees
- Cybersecurity Frameworks and Best Practices
- Cybersecurity Best Practices for Remote Workers
- Getting Started
- Accelerate Your Learning
- Summary
- Frequently Asked Questions
Why Cybersecurity Best Practices Fail
IBM's 2025 Cost of a Data Breach Report found that 63% of breached organisations lacked AI governance policies. Nearly all that suffered AI-related breaches (97%) had no proper access controls. These are foundational controls that every framework recommends.
The Compliance Trap. Most awareness programmes fail to create behavioural change. Only 32% of employees engage with cybersecurity awareness training (CybSafe, 2025). Among those who do, fewer than half change their behaviour. The knowing-doing gap is real: confidence in security knowledge rises while actual secure behaviours decline.
Annual training ignores the Ebbinghaus Forgetting Curve: individuals forget up to 80% of newly learned information within a month without reinforcement. A training session in January provides little protection against a phishing attack in November.
The Skills Gap Compounds Everything. This is not a headcount problem. Entry-level positions actually have a 10% worker surplus (Lightcast, 2024). The gap is in specific capabilities: AI security (41%), cloud security (36%), and risk assessment (29%).
The ISC2 2024 Cybersecurity Workforce Study found a global skills gap of 4.8 million professionals. Sixty-seven percent of organisations report staffing difficulties. Stretched teams default to reactive firefighting rather than proactive improvement.
For practitioners looking to develop in-demand skills, our Cybersecurity Skills Roadmap maps the path from foundational knowledge to job-ready capabilities.
Cybersecurity Measures and Best Practices That Work
Some controls appear in every framework because they work. Before expanding into advanced capabilities, organisations need these fundamentals operating consistently. Understand how they handle risk, not just what tools you have.
Zero Trust: Assume Breach, Verify Everything
Traditional perimeter security assumes everything inside the network is trusted. Attackers exploit this assumption. Once inside, they move laterally with minimal resistance, often using legitimate credentials and tools that blend into normal traffic.
Zero trust inverts this model: never trust, always verify. Every access request is authenticated and authorised regardless of where it originates. The 2025 Verizon DBIR found that credential abuse initiated 22% of breaches. Lateral movement after initial access often causes more damage than the initial compromise itself.
Least privilege is the enforcement mechanism. Users and systems receive only the access required for their specific function. When an account is compromised, the blast radius is contained. Attackers cannot pivot from a marketing workstation to production databases because that access path never existed.
Zero trust also forces honest conversations about legacy infrastructure. Systems that cannot support modern authentication or granular access controls become visible risks rather than hidden assumptions. Organisations face a choice: isolate legacy systems with compensating controls or accelerate migration. Either way, the risk is acknowledged rather than ignored.
Implementation does not require ripping out existing infrastructure overnight. Start with identity: strong authentication, conditional access policies, and privilege access management. Extend to network segmentation that limits lateral movement. Add continuous monitoring that detects anomalous access patterns. Each layer reduces the value of a compromised credential.
Multi-Factor Authentication
MFA remains the single most effective control against credential-based attacks. The 2025 Verizon DBIR found that 22% of breaches began with credential abuse and 88% of basic web application attacks involved stolen credentials.
The challenge is coverage, not technology. Shadow IT bypasses corporate identity. Exceptions accumulate until the control has more holes than protection. Effective implementation means treating MFA as non-negotiable for all systems that touch sensitive data.
Vulnerability Management That Keeps Pace
The 2025 Verizon DBIR shows vulnerability exploitation increased 34% year over year. Only 54% of edge device vulnerabilities get patched, with a median fix time of 32 days. That is an eternity when attackers are scanning continuously.
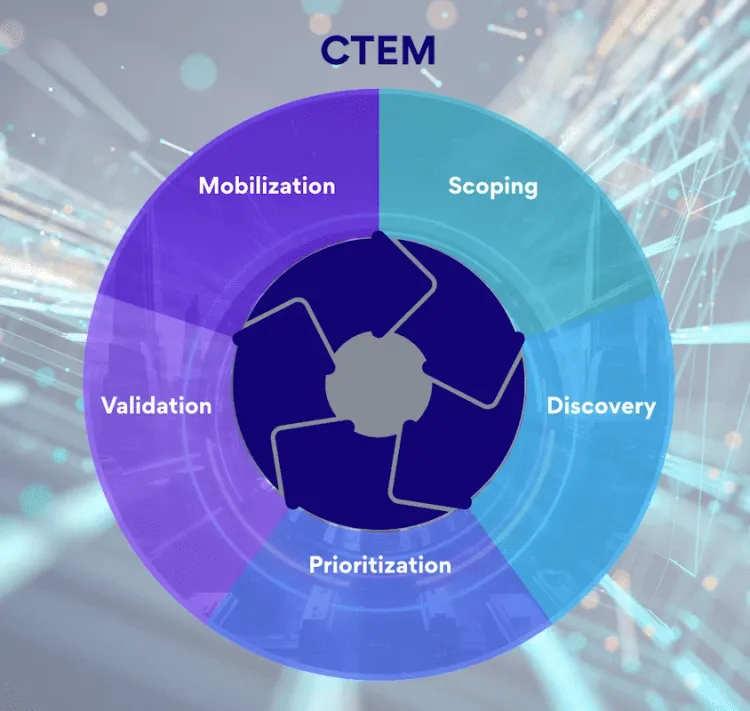
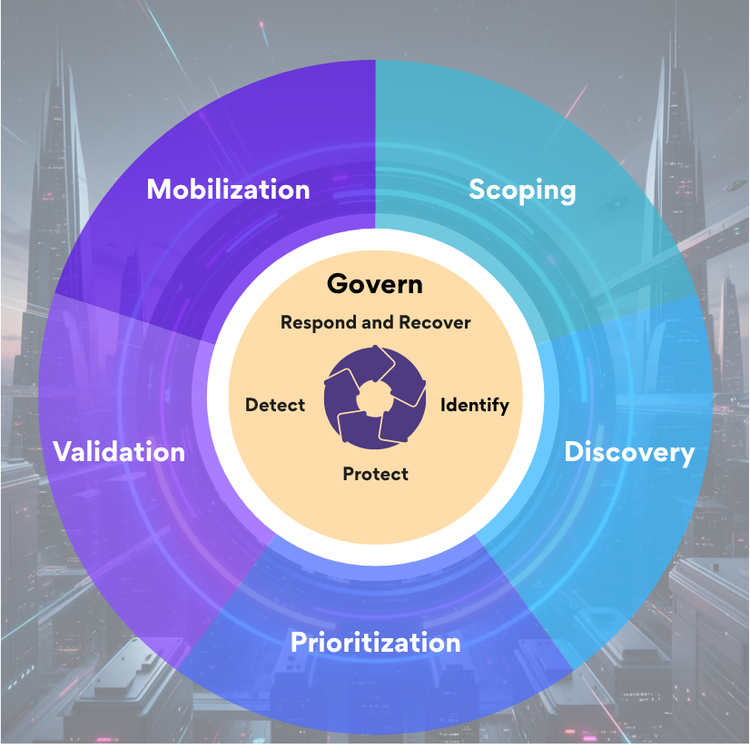
The shift toward continuous threat exposure management reflects this reality: organisations need to prioritise remediation based on actual risk, not just CVSS scores. The difference between effective and ineffective programmes comes down to ownership and clear SLAs.
For a deeper look at continuous exposure management, see the NIST-Aligned CTEM guide.
Cybersecurity Awareness Training That Changes Behaviour
Phishing simulation click rates plateau around 1.5% regardless of how much training organisations deliver (Verizon DBIR, 2025). But user reporting of suspicious emails increased fourfold after effective training programmes.
Its going to be difficult to eliminate all clicks. The goal should be building a culture where employees report suspicious activity quickly.
International Game Technology transformed from 30% phishing failure rates to 4-6% by implementing adaptive micro-learning, achieving 56% employee engagement. Brian Fontanella of Keystone Technology Consultants achieved a 50% reduction in risky behaviours within two months using behavioural training methods that leverage psychological principles rather than compliance checkboxes.
Building Detection and Response Capability
Prevention controls will fail. The organisations that limit breach impact are those that detect intrusions quickly and respond effectively.
Logging and Monitoring
The average breach lifecycle dropped to 241 days in 2025, the lowest in nine years (IBM). Organisations using AI-powered security tools extensively cut that lifecycle by 80 days and saved nearly $1.9 million on average.
Detection requires visibility. Effective monitoring starts with what matters: authentication events, privileged account usage, network traffic anomalies, and endpoint behaviour. Everything else is noise.
For organisations building detection capabilities, our ELK Stack Security Monitoring Tutorial provides a practical starting point for centralised logging.
Incident Response Planning
The 2025 IBM report found that 76% of organisations took more than 100 days to fully recover from a breach. Regular tabletop exercises and threat exposure assessments reveal gaps before real incidents expose them.
Securing the Supply Chain
Third-party involvement in breaches doubled year over year, now accounting for 30% of all incidents (Verizon DBIR, 2025). In 2021, Gartner predicted 45% of organisations would experience supply chain attacks by 2025. The reality exceeded the forecast: 75% have already experienced one (BlackBerry, 2024).
Supply chain breaches cost 17 times more to remediate than direct attacks. The average is $4.91 million globally, with U.S. organisations facing $10.22 million per incident.
Third-Party Risk Management
A questionnaire completed once during onboarding tells you nothing about a vendor's security posture two years later. Continuous monitoring provides more actionable intelligence than annual assessments.
Supply chain mapping is often the missing foundation. Which vendors have access to sensitive data? What happens if a key supplier goes offline?
Software Supply Chain Security
Sonatype documented 512,847 malicious packages in one year, a 156% year-over-year increase. For development teams, this means treating dependencies as attack surface. Security scanning must be part of the CI/CD pipeline.
Our npm Vulnerability Scanner guide covers practical approaches for JavaScript and Node.js environments.
How AI Is Reshaping Security Practice
AI is transforming cybersecurity from both sides. Attackers use it to scale phishing campaigns and automate reconnaissance. Defenders use it to accelerate detection and augment stretched teams.
The democratisation of AI tools has lowered barriers that once separated enterprise security from everyone else. For practitioners building skills, AI compresses the time from beginner to competent.
The 2025 threat landscape shows four shifts accelerating simultaneously: supply chain industrialisation, cloud identity targeting, social engineering automation, and AI-created attack surfaces. These are not isolated trends. They are interconnected vectors that compound each other's effectiveness.
AI security is now the top skills gap at 41% of organisations, overtaking cloud security for the first time (ISC2, 2025). Understanding both AI security threats and AI-powered defences positions practitioners for roles that barely existed two years ago.
The critical thinking rule applies more than ever: question everything AI tells you. AI confidently produces plausible-sounding nonsense.
Building Security Culture for Employees
Technology alone cannot solve security challenges. Security culture represents the collective behaviours that emerge when employees believe no one is watching.
Employees in organisations with poor security culture are 52 times more likely to share their login credentials during phishing attacks (KnowBe4, 2025). Teams experiencing emotional disengagement have nearly 3x as many internal security incidents. Teams operating in fear of retribution experience nearly 4x as many (Forrester, 2024).
The foundation is psychological safety. A culture where admitting "I clicked a suspicious link" triggers disciplinary action is a culture where incidents go unreported until they become breaches. Building a security culture should be advocated from the top, end users that make good decisions is the outcome of a healthy culture.
Measuring What Matters
Traditional metrics focus on activity: training completed, policies acknowledged. These tell you nothing about whether security is improving.
Leading indicators of cultural maturity: phishing reporting rate (target >55%), mean time to report suspicious activity (<5 minutes), validated user-reported incidents. These measure engagement and outcomes, not compliance.
Role-Based Training Investment
Not all employees face the same threats. Finance teams face business email compromise. IT administrators need training on privileged access protection. Development teams need security integrated into workflows.
BEC alone generated $2.77 billion in losses during 2024 (FBI). Concentrated risk justifies concentrated investment.
Cybersecurity Frameworks and Best Practices
Picking one framework and implementing it thoroughly beats addressing multiple frameworks superficially.
NIST Cybersecurity Best Practices
NIST CSF 2.0 provides comprehensive coverage across six core functions: govern, identify, protect, detect, respond, and recover. For enterprises subject to multiple regulatory requirements, mapping controls once to NIST CSF simplifies compliance across GDPR, HIPAA, PCI DSS, and sector-specific regulations.
CIS Controls offer a more prescriptive alternative. Implementation Group 1 covers essential cyber hygiene that every organisation should achieve first.
Cybersecurity Governance Best Practices
Security programmes fail when they lack executive support. The language of boards is financial impact: revenue loss from downtime, customer churn following breaches, regulatory penalties.
Return on Security Investment (ROSI) provides a framework for these conversations. A $50,000 investment that prevents $200,000 in breach losses yields a 3:1 return.
For practitioners aspiring to leadership conversations, understanding the full spectrum of cybersecurity career paths helps identify which skills to develop.
Cybersecurity Best Practices for Remote Workers
Distributed workforces expand the attack surface. Employees access corporate resources from home networks, personal devices, and public locations.
Secure access is non-negotiable. VPN or zero-trust network access should be mandatory. Split tunnelling creates risk.
Endpoint security must extend beyond the perimeter. Cloud-managed EDR provides visibility regardless of location.
Authentication becomes more critical. MFA for all remote access is baseline. Conditional access policies add additional assurance.
Training should address remote-specific risks. Phishing that impersonates IT support. Vishing that exploits inability to verify callers.
Getting Started
Comprehensive security programmes do not emerge overnight.
For resource-constrained teams, start with controls that address highest risks with lowest implementation cost: MFA across critical systems, regular backups with tested recovery, basic endpoint protection. CIS Implementation Group 1 covers essential cyber hygiene.
For maturing programmes, focus on visibility and response capability: centralised logging, detection rules tuned to your environment, incident response procedures tested through exercises.
For practitioners levelling up, the Cybersecurity Skills Roadmap breaks the journey into phases. The skills gap is not going away. Practitioners who develop capabilities in AI security, cloud, and risk assessment position themselves for the roles that matter most.
Accelerate Your Learning
Building security expertise takes time. The CyberDesserts Learning Assistant can help you explore specific topics, from threat actor techniques to framework implementation guidance.
Get explanations of controls and how they apply to your environment. Every response cites sources so you can verify and go deeper.
Summary
Cybersecurity best practices are well documented. What most organisations lack is not knowledge but consistent implementation.
The gap is in capability, not headcount. Compliance pressure incentivises checkbox behaviour. Metrics reward activity rather than outcomes.
Addressing these challenges means prioritising ruthlessly. Start with zero trust principles: assume breach, enforce least privilege, limit lateral movement. Layer detection and response capability because prevention will eventually fail. Treat security culture as a behavioural challenge, not a knowledge problem.
Start with where you are. Pick the gaps that represent your highest risk. Close them before moving to the next priority.
Get weekly security insights. Subscribe to CyberDesserts for practical threat intelligence and implementation guidance.
Frequently Asked Questions
What are the most important cybersecurity best practices for businesses?
MFA, timely vulnerability patching, and security awareness training that changes behaviour. These appear in every framework because the data shows they work.
Why do organisations struggle to implement cybersecurity best practices?
The knowing-doing gap. Teams know what to do but lack bandwidth to implement consistently. The global skills gap means teams are stretched thin. Compliance pressure incentivises checkbox behaviour.
What cybersecurity best practices should remote workers follow?
VPN or zero-trust access for corporate resources, MFA on every account, current security patches, clear guidance on handling sensitive data.
How long does it take to recover from a data breach?
IBM's 2025 research found 76% of organisations took more than 100 days to fully recover.
How can organisations measure security culture effectively?
Focus on behaviour, not compliance. Key metrics: phishing reporting rate (>55%), mean time to report suspicious activity (<5 minutes), validated user-reported incidents.
How is AI changing cybersecurity best practices?
AI reshapes security from both sides. Defenders use it for detection and augmentation. Attackers use it for convincing phishing and automated exploitation. AI security is the top skills gap at 41% of organisations.
Last updated: February 2026
References and Sources
- IBM Security. (2025). Cost of a Data Breach Report 2025. 241-day average breach lifecycle; 97% of AI-related breaches lacked access controls; 63% lacked AI governance policies.
- Verizon. (2025). 2025 Data Breach Investigations Report. 60% human element; 22% credential abuse; 30% third-party; vulnerability exploitation up 34%.
- ISC2. (2024). Cybersecurity Workforce Study. Global skills gap 4.8 million; AI skills (41%) top demand.
- Lightcast. (2024). Quarterly Cybersecurity Talent Report. Entry-level 10% worker surplus.
- CybSafe. (2025). Oh, Behave! Report. Only 32% engage with training; fewer than half change behaviour.
- KnowBe4. (2025). Security Culture Report. Poor cultures 52x more likely to share credentials.
- Forrester Research. (2024). Security Culture Impact Study. Disengaged teams 3x more incidents; fear-based 4x.
- BlackBerry. (2024). Supply Chain Security Survey. 75% experienced supply chain attacks.
- FBI. (2024). Internet Crime Report. BEC $2.77 billion in losses.
- NIST. (2024). Cybersecurity Framework 2.0.
Member discussion