ClickFix Attacks: How They Work and How to Stop Them
Updated February 2026: Added ClickFix-as-a-Service (ErrTraffic), DNS TXT record delivery (KongTuke), CrashFix browser extension variant, ConsentFix OAuth hijacking, expanded detection
When AI Writes the Code, Who Catches the Bugs?
In December 2025, Boris Cherny, creator of Anthropic's Claude Code, revealed he hadn't opened an IDE
Hacktivist DDoS Attacks: A Defender's Guide
NoName057(16) has targeted 3,700+ hosts in thirteen months. Their playbook is predictable: strike during elections, holidays, and geopolitical flashpoints. Here's what the La Poste attack reveals about defending against hacktivist DDoS.
14 Crypto Scams to Watch For in 2026
Cryptocurrency scam losses reached $9.3 billion in the United States alone in 2024, a 66% increase from the previous
MongoBleed Exploit: The MongoDB Memory Leak Hitting 87,000 Servers
Updated January 10, 2026: CISA's remediation deadline for federal agencies is January 19. Ubuntu has retracted its claim
Prompt Injection Attacks: Examples, Techniques, and Defence
Researchers tested 36 LLM-integrated applications and found 31 vulnerable to prompt injection. That is an 86% failure rate (HouYi Research,
Building a Second Brain for Cybersecurity Work
Sixty-five percent of security professionals report their job has become harder in the past two years (ISSA/ESG, 2024). New
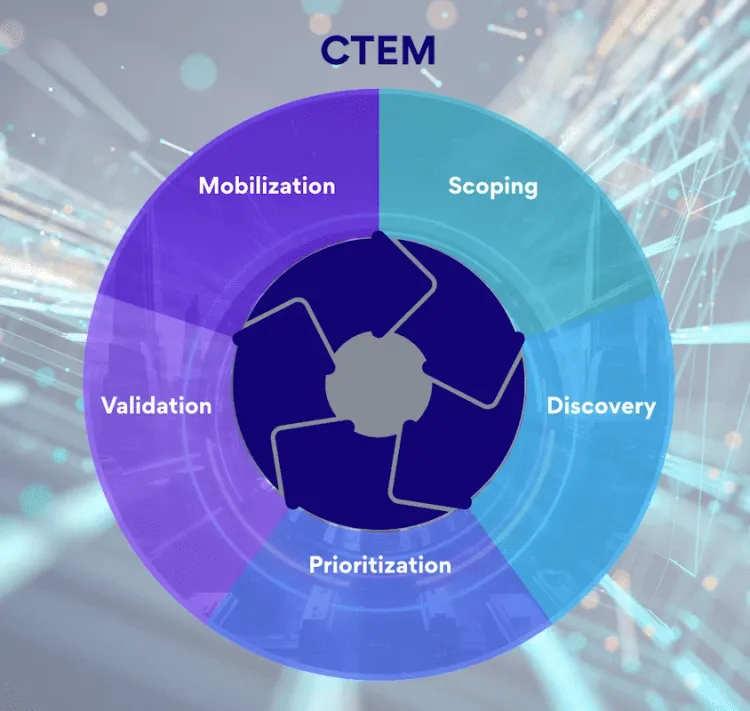
What is CTEM? Complete Guide to Continuous Threat Exposure Management
Gartner predicts that by 2026, organisations prioritising security investments based on a CTEM program will suffer two-thirds fewer breaches. Meanwhile,
npm Security: The Complete Guide to Package Vulnerabilities
npm processes 4.5 trillion package requests annually, representing 70% year-over-year growth (Sonatype, 2024). This scale makes the JavaScript ecosystem
Cybersecurity Career Path: Complete Guide for 2026
59% of organisations now report critical or significant cybersecurity skills gaps, up from 44% last year (ISC2, 2025). The narrative