Infostealers in 2026: How They Work and How to Stop Them

Updated January 2026: Comprehensive 2025 statistics, expanded detection guidance, and post-Lumma disruption landscape analysis.
Infostealer malware stole 1.8 billion credentials in the first half of 2025 alone. That is an 800% increase over the previous six months (Flashpoint, 2025). The stolen credentials came from 5.8 million infected devices.
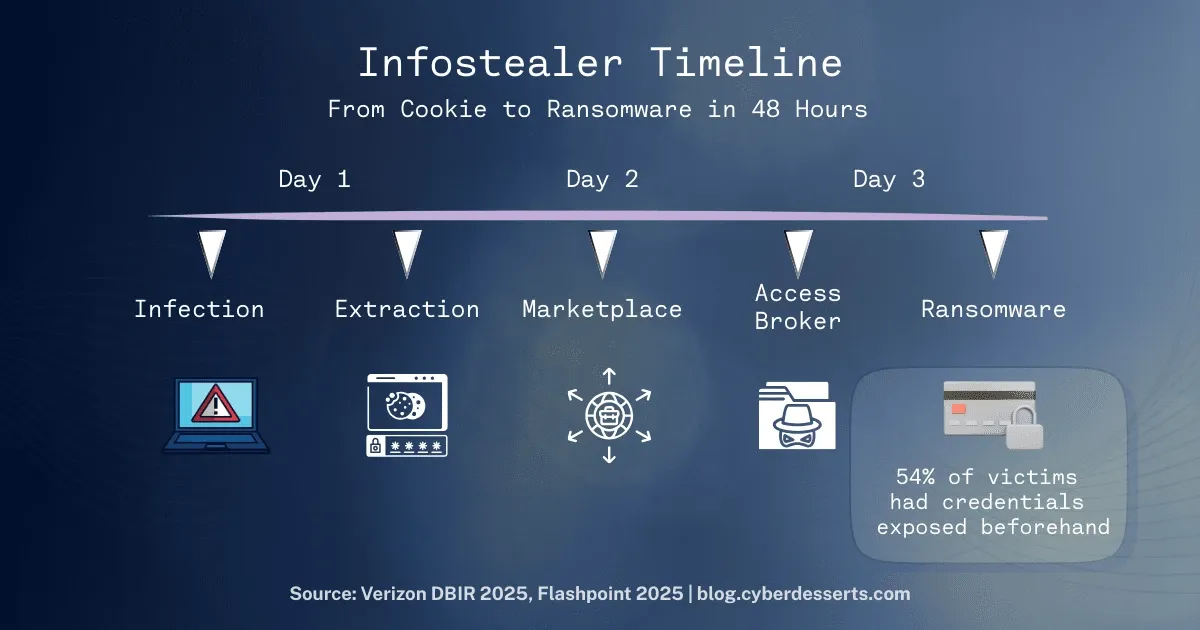
54% of ransomware victims had their domain credentials appear in stealer log marketplaces before the attack hit (Verizon DBIR, 2025). The time between stolen credential and ransomware deployment? Sometimes under 48 hours.
Browser cookies are a common attack vector target. Your security programme should be hunting for infostealer infections to stay on top of this attack vector.
Get articles like this delivered to your inbox. Subscribe to CyberDesserts for practical security insights.
What Are Infostealers?
Infostealers are malware designed to harvest sensitive information from infected devices and transmit it to attackers. They operate quietly. Most victims never know they were compromised, that is the point.
What they steal:
- Browser credentials (saved passwords, autofill data)
- Session cookies and authentication tokens
- Cryptocurrency wallet keys and seed phrases
- VPN and RDP configurations
- Email client data
- Files matching specific patterns (documents, keys, configs)
- System information (hostname, IP, installed software)
The business model has proven successful. Developers build the malware and sell subscriptions. Operators buy access, distribute the malware, and either use the stolen data themselves or sell it to others. The average cost for a malware-as-a-service infostealer subscription is $200 per month (KELA, 2025).
That low barrier to entry matters. You don't need technical sophistication to deploy infostealers. You need $200 and a distribution method.
The stolen data gets packaged into "stealer logs" and sold on underground markets or distributed through Telegram channels. Initial access brokers parse these logs for valuable enterprise credentials and sell verified network access to ransomware operators.
This supply chain is what makes infostealers dangerous. They are the first domino. A single infected workstation becomes a gateway to the corporate network, partner systems, and supply chain access.
How Infostealers Work
Infostealers need to reach victim machines, extract data, and exfiltrate it without detection. Each stage has evolved significantly.
Infection Vectors
Phishing remains dominant. IBM X-Force observed an 84% year-over-year increase in infostealers delivered via phishing emails in 2024. The messages typically carry malicious attachments or links to compromised sites.
Malvertising and trojanised software account for significant infections. Cracked software, fake updates, and poisoned search results all serve as distribution channels. If someone downloads pirated software or clicks a suspicious "download" button, they may be installing an infostealer alongside whatever they expected.
Fake CAPTCHA campaigns emerged as a major vector in 2024-2025. Attackers compromise legitimate websites and display fake verification pages. Victims are instructed to paste commands into their system's Run utility to "pass verification." Those commands download and execute malware directly in memory.
This technique, sometimes called ClickFix, exploits user trust in familiar verification patterns. It bypasses many traditional defences because users voluntarily execute the payload.
Data Extraction
Once running, infostealers systematically harvest data from predictable locations.
Browser data is the primary target. Infostealers access browser databases containing saved passwords, cookies, autofill data, and browsing history. Most browsers store this data in SQLite databases at known file paths.
Form grabbing intercepts data as users submit it. Rather than extracting stored credentials, the malware captures information in real-time as victims type.
Keylogging records keystrokes to capture credentials for sites where users don't save passwords.
File scanning searches for documents, private keys, cryptocurrency wallet files, and configuration files matching specified patterns. Think about where sensitive data might be stored.
MFA Bypass via Session Cookies
This is the detail that changes defensive calculations.
Traditional MFA protects against password theft. If an attacker has your password but not your second factor, they cannot authenticate. Infostealers bypass this by stealing session cookies and authentication tokens.
When you log into a site with MFA, the site issues a session cookie. That cookie proves you already authenticated. Infostealers harvest these cookies. Attackers replay them to access accounts without needing the password or MFA token.
In 2024 alone, malware lifted over 17 billion browser cookies (aggregated industry data). Many of those cookies were valid authentication sessions for corporate services.
This is why "enable MFA" is necessary but not sufficient. MFA protects the authentication event. It does not protect the authenticated session from being stolen afterward. This is a significant loophole that should be addressed.
The Stealer Log Economy
Stolen credentials become commodities in a structured underground economy.
Telegram Channels
Telegram has become the primary distribution platform for stealer logs. Operators run public channels to build reputation, offering free samples to demonstrate quality. Private channels require paid subscriptions ranging from $100 to $500 per month.
Some threat actors sell access to "live logs" where stolen data streams directly as infections occur. Speed matters in this market. Fresh credentials have higher value than stale ones.
Underground Marketplaces
Traditional cybercrime forums and marketplaces like Russian Market trade bulk credential dumps. Individual listings often bundle hundreds or thousands of stolen credentials.
The ecosystem segments by buyer type. Low-tier criminals buy bulk dumps for credential stuffing attacks. More sophisticated actors, including initial access brokers, parse logs for high-value enterprise credentials.
Initial Access Broker Pipeline
Initial access brokers specialise in converting raw credentials into verified network access. They identify corporate VPN logins, RDP credentials, and SaaS admin accounts within stealer logs. They validate access, then sell it to ransomware operators.
The window between stolen credential and ransomware deployment has compressed dramatically. Verizon's 2025 DBIR found the most common timing was just 2 days between credential appearing in a stealer log and ransomware incident.
If your credentials appear in a stealer marketplace on Monday, you may be dealing with ransomware by Wednesday.
The Infostealer Families Dominating 2026
Not all stealers are equal. Three families account for over 75% of infections (KELA, 2025).
Lumma Stealer
Lumma dominated the landscape until May 2025, when coordinated law enforcement action disrupted its infrastructure. Microsoft and partners sinkholed 394,000 infected Windows hosts in a two-month period.
Before disruption, Lumma was the most prevalent infostealer by volume. Its distinguishing features included direct syscall execution to evade EDR hooks, anti-sandbox evasion, and stealth exfiltration techniques.
Lumma was notably associated with Scattered Spider operations and was distributed through fake CAPTCHA campaigns at scale.
The disruption reduced Lumma's prevalence, but did not eliminate it. Security teams should anticipate operators migrating to alternative stealers.
StealC
StealC ranks among the top three globally by infection volume. Its developers prioritise stealth over capability breadth.
Version 2, released in March 2025, added command and control encryption with RC4 and updated payload delivery options including MSI packages and PowerShell. These changes made StealC more evasive and adaptable.
The design philosophy emphasises reducing alerting. StealC generates less noise than competitors, which helps it avoid detection in environments with security monitoring.
RedLine
RedLine has been a workhorse of the infostealer ecosystem for years. Commonly delivered via phishing attachments, it uses regex-based data harvesting to extract credentials and cookies from browsers.
RedLine infections have contributed to millions of stolen credentials annually. Its longevity reflects consistent updates and reliable operation.
Vidar
Vidar surged in prevalence following Lumma's disruption. Trend Micro analysts noted that as Lumma declined, security teams should anticipate increased Vidar 2.0 activity.
Vidar's 2025 overhaul completely rewrote the codebase for efficiency and stealth. It targets personal information, browser data, and cryptocurrency wallet details.
Notably, Vidar uses social media platforms like Telegram and Mastodon for command and control infrastructure. Some samples contain null bytes to inflate file size and evade antivirus detection.
AMOS (Atomic macOS Stealer)
AMOS represents the expansion of infostealers beyond Windows. The latest versions include persistent backdoor capability that survives system reboots.
Distribution methods include fake applications and cloned Homebrew installers. AMOS bypasses Gatekeeper protections and has been active in over 120 countries.
If your organisation has significant macOS deployment, AMOS demonstrates that these threats are cross-platform. macOS is not immune.
Real-World Impact: From Stolen Cookie to Ransomware
The connection between infostealers and major incidents is not theoretical.
Airline: VPN Credential to Ransomware
A European airline breach demonstrated the full attack chain. Attackers obtained VPN credentials through infostealer malware. Those credentials provided initial access to the corporate network.
From that foothold, attackers escalated privileges and deployed ransomware. The entire progression from stolen credential to ransomware detonation followed the pattern security teams see repeatedly.
What was missing: MFA on VPN access and strict network access controls. A single stolen credential should not provide unfettered network access.
Financial Services BEC via Raccoon Stealer
An FBI advisory documented a multimillion-dollar business email compromise traced to Raccoon Stealer infections. Attackers used stolen browser cookies to take over email accounts without triggering authentication alerts.
With email access, attackers monitored communications and executed wire fraud. The organisation discovered the compromise only after funds were gone.
What was missing: Browser hardening policies, session management, and monitoring for credential exposure in underground markets.
The Supply Chain Multiplier
Many stolen credentials provide third-party or supply chain access. A single infected workstation at a managed service provider becomes a gateway to every client network they manage.
This is what transforms infostealers from nuisance malware into strategic threats. The compromised credentials may not belong to high-value targets directly. They belong to someone with access to high-value targets.
For more on supply chain risk, see Gartner's 2025 Supply Chain Prediction: A Retrospective.
How to Detect Infostealer Activity
Detection requires visibility at multiple layers. No single control catches everything.
Network-Level Indicators
Suspicious outbound connections. Infostealers communicate with command and control infrastructure. Watch for connections to unclassified domains, particularly POST requests with encoded payloads.
DNS anomalies. Some stealers use DNS for C2 communication or domain generation algorithms. Unusual query patterns may indicate infection.
Data volume anomalies. Credential exfiltration produces smaller data transfers than traditional data theft, but patterns may still be detectable.
Endpoint Behavioural Indicators
Process hollowing. Lumma and other advanced stealers use process hollowing to inject malicious code into legitimate processes. Monitor for this technique.
Direct syscall patterns. Lumma's signature behaviour includes direct syscalls to evade EDR hooks. EDR tools increasingly detect this, but coverage varies.
Browser data access. Legitimate processes rarely access browser credential databases directly. Alert on unusual processes reading SQLite databases from browser profile directories.
Unusual DLL activity. Watch for DLLs loaded from unexpected locations or with suspicious characteristics.
Check the section below on technical controls for more detailed info on EDR solutions.
Threat Hunting Approaches
If you operate a SIEM, hunt for these patterns:
- Processes accessing browser profile directories that are not the browser itself
- Outbound connections to recently registered domains
- PowerShell or cmd.exe spawned from Office applications
- Credential store access outside normal user workflows
This could prove useful as an exercise combined with the ELK Stack Security Monitoring Tutorial.
For detection rule development, Florian Roth's work on YARA rules and Sigma rules provides excellent starting points. His detection methodology has become a community standard.
Credential Monitoring
Proactively search for your corporate domains in stealer log marketplaces. Several threat intelligence services provide this capability. Finding your credentials in a marketplace before attackers use them gives you a window to respond.
The window is small. Days, not weeks.
How to Protect Against Infostealers
Protection requires technical controls, process discipline, and user awareness. No single measure is sufficient.
Technical Controls
Disable browser password storage for sensitive applications. Corporate SSO, financial systems, and admin consoles should not have credentials saved in browsers. This reduces what infostealers can harvest.
Deploy EDR with behavioural detection. Signature-based antivirus misses novel variants. Behavioural detection catches techniques even when specific malware is unknown. Not all EDR products detect infostealers equally. Evaluate coverage for stealer-specific behaviours, but make sure this is not your only defence. Having spent many years working for an EDR vendor, I can tell you first hand even with a good solution defence in depth is still crucial as detection is not guaranteed.
Enforce MFA everywhere. Yes, session cookies bypass MFA. Deploy it anyway. MFA still protects against password-only attacks and raises the bar for attackers. It is necessary, not sufficient.
Implement Device Bound Session Credentials where available. Chrome introduced Device Bound Session Credentials (DBSC) to prevent session cookie replay attacks. DBSC ties authentication sessions to specific devices using TPM-backed cryptographic keys. When a session starts, Chrome generates a public/private key pair stored securely on the device. The server can verify proof-of-possession throughout the session, making stolen cookies useless on other devices.
Chrome's second Origin Trial runs October 2025 to February 2026. Microsoft Edge and identity providers like Okta have expressed interest in the standard. This directly addresses the session hijacking problem, though adoption is still early and currently limited to Windows devices with TPM hardware.
Reduce local admin rights. Infostealers running with admin privileges can access more data and evade more defences. Principle of least privilege limits blast radius.
Browser hardening. Disable unnecessary extensions. Consider browser isolation for high-risk users. Evaluate enterprise browsers with enhanced security controls.
Process Controls
Credential exposure monitoring. Subscribe to threat intelligence services that monitor underground markets for your domains. When your credentials appear, you need to know immediately. A good threat intel feed will give you detailed information, sometimes including the target IP and source of the credential exposure.
Rapid response playbooks. Define what happens when credentials appear in stealer logs. Password resets, session invalidation, endpoint investigation. The 48-hour window means you cannot wait for the next change control meeting.
Regular session invalidation. Periodically force re-authentication for sensitive systems. This limits the useful lifetime of stolen session cookies.
Third-party access reviews. Understand which partners and vendors have access to your systems. Their infections become your problem.
Human Factors
Phishing awareness that sticks. 84% of infostealer delivery is phishing. Generic annual training is not enough. Role-specific scenarios, simulated campaigns, and consequences for repeated failures.
Cracked software policies. Make it clear that installing pirated software on corporate devices is a firing offense. Make it equally clear that you will provide legitimate tools employees need.
Personal device policies. 35% of infostealer infections occur on personal devices (KELA, 2025). Remote work means personal machines often contain corporate credentials. Define acceptable use, enforce MDM where possible, and consider separate browser profiles for work. My advice: avoid managing personal devices if you can. It's another headache and significantly expands your attack surface.
The AI Factor
AI is changing both attack delivery and malware development.
AI-generated phishing. Over 82% of phishing emails now show evidence of AI generation (industry estimates, 2025). AI-crafted lures are more convincing, more personalised, and produced at scale.
Polymorphic code. Malware authors use AI to generate code variants that evade signature detection. The cat-and-mouse game between malware and antivirus accelerates.
This does not fundamentally change defensive strategy. It raises the bar. Phishing awareness must account for more sophisticated social engineering. Detection must rely more heavily on behaviour than signatures. Let's see how this evolves in 2026. It's likely every layer of your defensive strategies will be tested when it comes to AI.
Summary
Infostealers are the first stage in enterprise compromises. Stolen browser cookies become the initial path for ransomware deployment or business email compromise.
In numbers: 1.8 billion credentials stolen in six months. 54% of ransomware victims had credentials exposed beforehand. A 48-hour window between credential theft and ransomware.
This should help take your defensive strategies to the next level.
Defensive priorities:
- Deploy EDR with behavioural detection for stealer techniques
- Monitor for credential exposure in underground markets
- Build rapid response capability for the 48-hour window
- Disable browser password storage for sensitive systems
- Train users on phishing with role-specific scenarios
- Address personal device risk in your security programme
Infostealers may look like small-scale threats. They warrant enterprise-grade defences. Treat them as strategic risks and position your organisation as a hardened target.
Frequently Asked Questions
What is an infostealer?
An infostealer is malware designed to secretly harvest sensitive information from infected devices. They target credentials, session cookies, cryptocurrency wallets, and personal files. Most operate as malware-as-a-service, available for around $200 per month.
How do infostealers steal passwords?
Infostealers extract passwords from browser databases, intercept data submitted in web forms (form grabbing), and record keystrokes (keylogging). They also steal session cookies, which allow attackers to access accounts without needing the password at all.
What is the most common infostealer?
As of early 2026, Lumma, StealC, and RedLine account for over 75% of infections globally. Lumma's infrastructure was disrupted in May 2025, leading to increased activity from StealC and Vidar as operators migrated.
Can MFA stop infostealers?
Not entirely. MFA protects the authentication event, but infostealers steal session cookies that represent already-authenticated sessions. Attackers replay these cookies to access accounts without needing passwords or MFA codes. FIDO2 passkeys offer stronger protection against this technique.
How do I know if I'm infected with an infostealer?
Most infections produce no obvious symptoms. Detection relies on EDR alerts for suspicious browser data access, monitoring for credentials appearing in dark web markets, and network analysis for unusual outbound connections. If you suspect infection, investigate immediately. Do not wait for confirmation.
What should I do if my credentials appear in a stealer log?
Reset passwords immediately for affected accounts. Invalidate active sessions. Investigate the source endpoint for malware. Review access logs for suspicious activity. Assume attackers have already attempted to use the credentials.
This analysis gets updated as the threat landscape shifts. Subscribers receive notifications when major changes happen, plus weekly practical security content.
Last updated: January 2026
References and Sources
- Flashpoint. (2025). Global Threat Intelligence Index: 2025 Midyear Edition. 1.8 billion credentials stolen from 5.8 million devices in H1 2025, 800% increase.
- Verizon. (2025). 2025 Data Breach Investigations Report. 54% of ransomware victims had domains in stealer logs. 88% of web app attacks involve stolen credentials.
- KELA. (2025). Infostealer Epidemic Report. 3.9 billion credentials compromised, 4.3 million devices infected in 2024. Top three families: Lumma, StealC, RedLine.
- IBM X-Force. (2025). Threat Intelligence Index. 84% YoY increase in infostealers via phishing.
- Microsoft. (2025). Lumma Stealer Disruption. 394,000 infections sinkholed in coordinated action.
- CISA. (2025). Alert AA25-141b. Threat actors deploy LummaC2 malware advisory.
- Google Chrome. (2025). Device Bound Session Credentials. Origin Trial documentation.





Member discussion