The Shadow AI Crisis: And What You Can Do

90% of IT leaders are concerned about Shadow AI (Komprise). Meanwhile, 313,120 paste attempts were logged in a single month across enterprise systems (Menlo Security). If your organization isn't actively governing AI use, you're already exposed to risks you can't even see.
I don't want to paint a picture of gloom as there are many opportunities that will transform every aspect of what we do. but the rapid adoption of AI requires a solid strategy not to mention the fallout from over hype there will be many failures before we see the successes. Another interesting point is that what we see today will be very different 2-5 years down the line as the AI thinking capability grows exponentially every 7 months. The 2014 movie Lucy comes to mind.
The Shadow AI Problem
Your employees are already using AI whether you've approved it or not. Just take a look at the numbers:
- 6,500+ GenAI domains and 3,000 apps are in circulation (Menlo Security)
- 62% of employees can't identify which AI tools comply with GDPR (MIT Sloan)
- 80% of organizations have experienced negative outcomes from unauthorized AI use (Komprise)
- 13% report financial losses, customer fallout, and reputational damage from Shadow AI
- $650,000+ average cost per AI-associated breach (IBM)
The data being shared isn't just marketing copy. It includes customer information, internal documents, financial data, and proprietary code. Without clear policies, well-meaning employees inadvertently create compliance violations and security risks.
Why Traditional Security Can't Keep Up
What makes Shadow AI particularly concerning is its integration within approved tools. 18% of organizations worry about GenAI features embedded within authorized SaaS applications capabilities often enabled automatically in Zoom, Salesforce, and Adobe (Acuvity). Thats impacting security leaders who are overwhelmed with requests.
Employees may unknowingly use AI functionality that's analyzing and processing company data. Traditional security approaches fail because they focus on blocking unauthorized applications, but Shadow AI often operates within authorized software or through browser-based interfaces that bypass corporate controls.
The vulnerability is most acute at runtime. 38% of security leaders identify runtime as their most vulnerable phase, with 27% admitting it's where they're least prepared (Acuvity). Unlike traditional software that reveals risks during development, AI systems only expose their full threat profile when processing real data in production.
The Adoption-Security Disconnect
Here's the paradox: While 23% of organizations report scaling agentic AI systems (McKinsey), 95% of AI pilot programs fail to achieve rapid revenue acceleration (MIT). The disconnect between ambition and execution is becoming obvious:
- 42% of C-suite executives say AI adoption is "tearing their company apart" (Writer)
- Only 45% of employees believe their organization has successfully adopted AI, versus 75% of the C-suite
- 40% of enterprises lack adequate AI expertise internally (Stack AI)
- 60% cite legacy system integration and compliance as primary barriers (Deloitte)
Companies with formal AI strategies report 80% success in adoption, compared to just 37% for those without. Which tells us governance is the difference between success and chaos.
Building Your AI Defense Strategy
Success requires a holistic approach across four critical domains:
1. Governance & Policy
Start with an AI Acceptable Use Policy that clearly defines permitted tools and data handling procedures. Check our AI Security FAQ for common governance questions and framework guidance.
2. Technical Controls
Deploy AI discovery and monitoring solutions. Firms with internal AI portals saw a 65% drop in Shadow AI within six months (IDC). Create sanctioned alternatives that meet both security requirements and user needs.
3. Data Security
With 49% of organizations expecting Shadow AI incidents within 12 months (Acuvity), visibility becomes critical. Monitor what data flows to AI systems and implement DLP controls specifically configured for AI endpoints.
4. Human Factors
Transform security from enforcement to enablement. When employees understand risks and have secure alternatives, compliance becomes collaborative rather than combative.
But here's the challenge security leaders face: Which domain do you tackle first? Where are the quick wins?
Most organizations waste months building comprehensive AI governance frameworks when they should be running an initial assessment and addressing their most critical gap first to get those quick wins.
The Bottom Line
With AI adoption accelerating 32% of enterprises predict workforce reductions while simultaneously hiring for AI roles (McKinsey) the window for establishing governance is closing. Organizations face a choice: lead the transformation or be led by it.
Your AI security strategy must address the emerging threat landscape, implement robust controls for AI capabilities, and prepare for 2025's evolving security environment.
But governance is only the start. As I've discussed in my analysis of Gartner's predictions, the gap between prediction and reality in AI security is widening. A robust AI security strategy requires continuous assessment across all four domains.
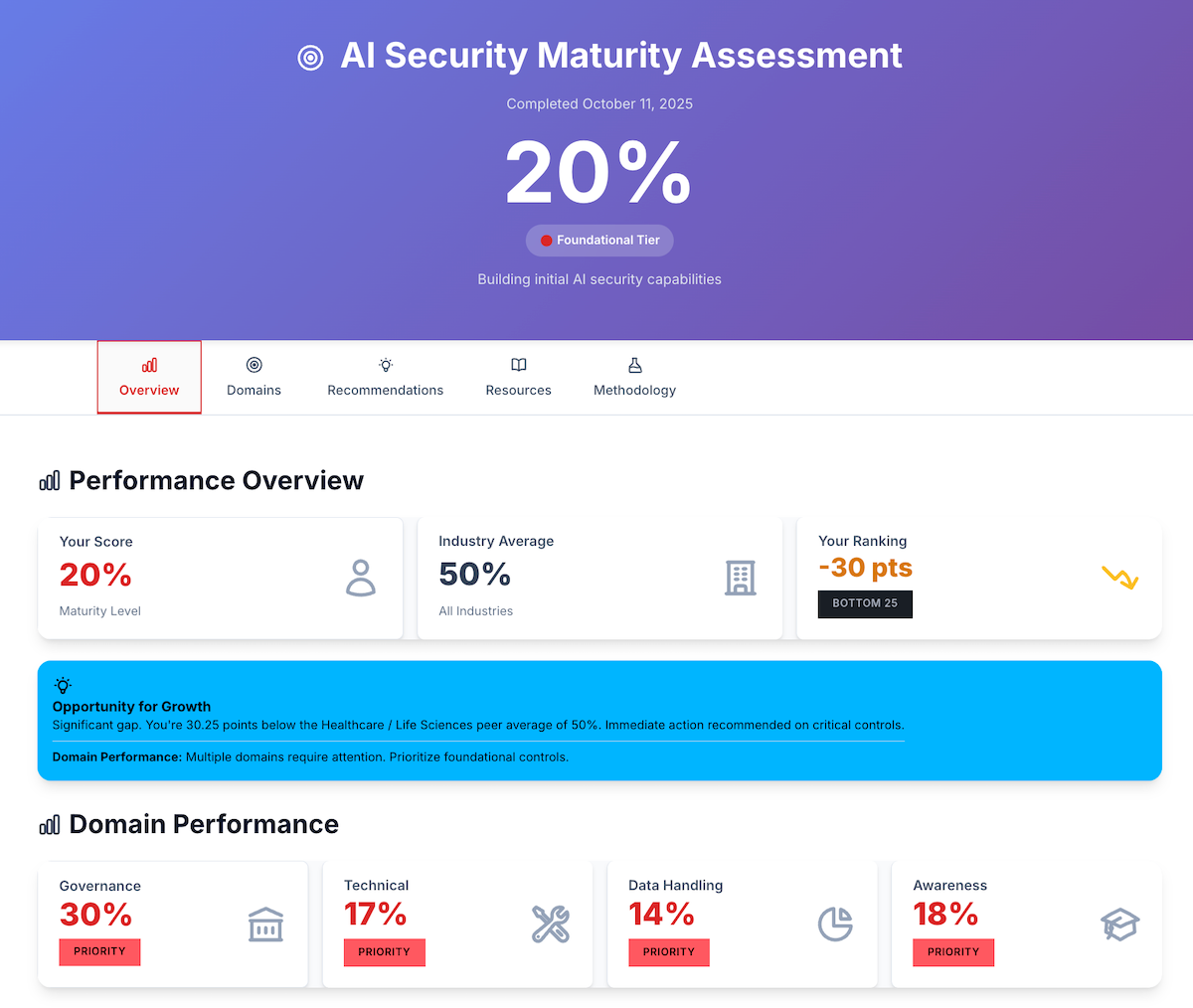
Ready to see where you stand? Take the free AI Security Readiness Assessment you don't need to share your personal details just a simple questionnaire that will instantly give you a roadmap on your AI security posture across governance, technical controls, data security, and human factors.
Key Resources:
References:
- Komprise (2025). "IT Survey: AI, Data & Enterprise Risk." Survey of 200 IT directors.
- Menlo Security (2025). "How AI is Shaping the Modern Workspace."
- MIT Sloan & MIT NANDA (2024-2025). "GenAI Divide: State of AI in Business."
- IBM (2025). "Cost of Data Breach Report."
- McKinsey (2025). "The State of AI in 2025."
- Writer (2025). "Generative AI adoption in the enterprise." Survey of 1,600 knowledge workers.
- Deloitte (2025). "AI trends 2025: Adoption barriers."
- Stack AI (2025). "The 7 Biggest AI Adoption Challenges."
- Acuvity (2025). "2025 State of AI Security."
- IDC (2024). Internal AI portal effectiveness study.
Member discussion