Why NIST Aligned CTEM Is the Framework Integration Security Teams Actually Need
How confident are you that your NIST implementation catches threats before they become incidents? Most security teams I work have implemented the NIST Cybersecurity Framework diligently documenting controls, conducting assessments, achieving their target profiles, there's a concerning gap between governance maturity and operational reality.
Here's what nobody talks about: frameworks like NIST CSF 2.0 excel at defining what outcomes you should achieve, but they don't tell you whether those outcomes are actually working against real-world attack techniques. That's where NIST aligned CTEM changes the conversation entirely.
Beyond Point-in-Time Assessment
NIST CSF 2.0's Implementation Tiers provide an excellent maturity progression from Tier 1's ad hoc responses through Tier 4's adaptive, continuously improving approaches. The challenge? Even organizations operating at Tier 3 or 4 often rely on periodic assessments that capture a moment in time rather than continuous validation.
Continuous Threat Exposure Management operates on a fundamentally different principle. Rather than assessing controls at intervals, CTEM creates a perpetual cycle of discovering, prioritizing, validating, and remediating exposures based on the current threat landscape. It's the operational engine that makes NIST's adaptive tier genuinely adaptive.
The Natural Integration Points
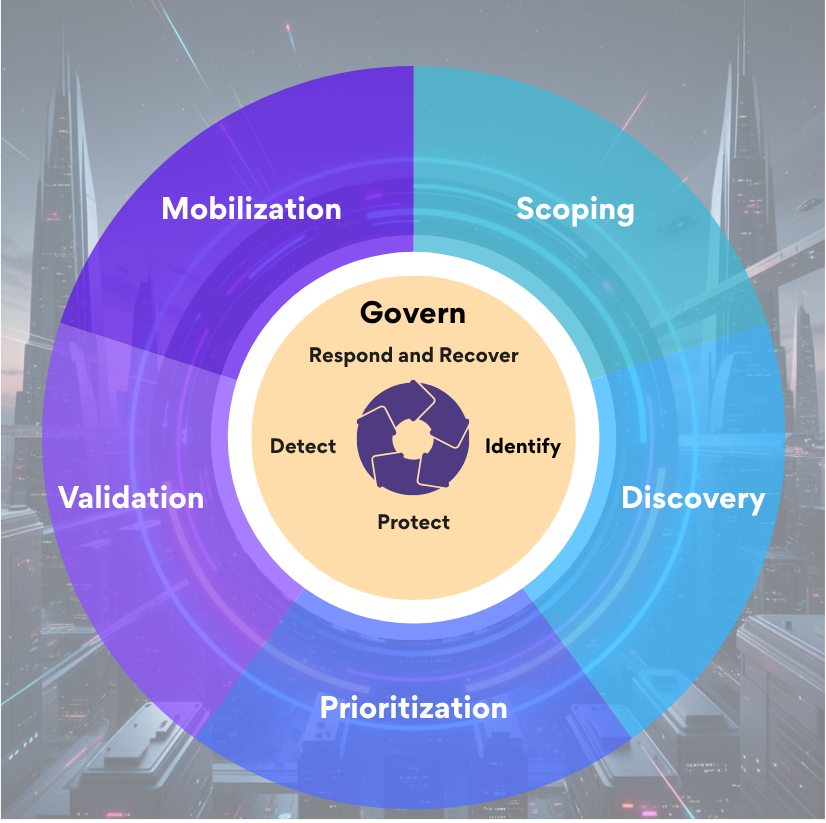
When you map CTEM's five stages against NIST CSF 2.0's six functions, the alignment isn't just convenient, it's transformative:
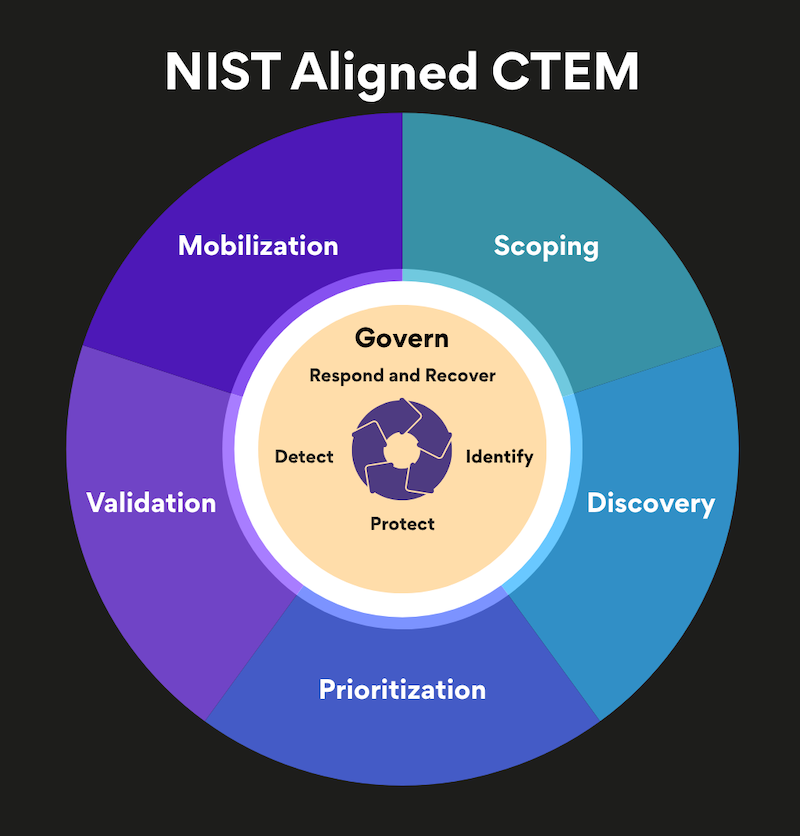
Govern meets scoping and mobilization. NIST's Govern function establishes cybersecurity risk management strategy and organizational context. CTEM's scoping phase operationalizes this by defining exactly which assets, attack surfaces, and third-party dependencies matter most to your mission. The mobilization stage then ensures resources align with governance priorities for maximum effectiveness and this becomes the core success criteria.
Identify becomes continuous discovery. NIST asks organizations to identify their assets, risks, and vulnerabilities. CTEM transforms this from a periodic inventory exercise into automated, continuous discovery that captures shadow IT, forgotten assets, and evolving attack surfaces in real time.
Protect gains validation through testing. You've implemented security controls based on NIST guidance. But do they actually stop the attacks you care about? CTEM's validation stage maps your exposures to compensating controls and tests whether they effectively mitigate specific attacker tactics and techniques. It answers the question most frameworks avoid: "Would this control stop a real attack?"
Detect improves through threat contextualization. NIST's Detect function focuses on identifying cybersecurity events. CTEM enhances this by continuously assessing which exposures are most likely to be exploited based on threat actor interest, active campaigns, and observed exploitation patterns. Staying current with these patterns requires monitoring threat intelligence feeds and security news systematically. Not all vulnerabilities deserve the same urgency.
Respond becomes risk-prioritized action. Generic CVSS scores don't tell you what to fix first. CTEM's prioritization through risk context considers actual exploitability in your specific environment, business impact of compromise, and effectiveness of compensating controls. This transforms NIST's Respond function from reactive to strategically proactive.
Recover strengthens through root cause focus. When incidents do occur, CTEM's approach to remediation emphasizes addressing root causes rather than symptomatic fixes, aligning perfectly with NIST's emphasis on lessons learned and continuous improvement.
From Compliance Theater to Operational Reality
Working with organizations across EMEA, I've seen a pattern: those treating frameworks purely as compliance checkboxes struggle with the gap between documented controls and actual security posture. Meanwhile, teams that integrate CTEM principles into their NIST implementation operate differently. They move beyond asking "Have we implemented this control?" to "Is this control effective against current threats?"
This shift matters because threat actors don't care about your framework maturity tier. They care about exploitable weaknesses. A NIST aligned CTEM approach ensures your governance decisions, risk prioritization, and resource allocation reflect the threats actually targeting your organization.
Measuring What Matters
NIST CSF 2.0 emphasizes outcome-based approaches. CTEM provides the metrics to validate those outcomes continuously:
- Mean Time to Conclude replaces traditional MTTR with complete incident lifecycle management
- Threat Detection Coverage measures what percentage of relevant MITRE ATT&CK techniques you can actually detect
- Alert Investigation Rate aims for 100% coverage versus the 19% industry average where most alerts go uninvestigated
- Exposure Validation Frequency tracks how often you're testing whether controls work as intended
These metrics don't replace NIST's outcomes: they prove whether you're achieving them.
Making It Practical
If you're already implementing NIST CSF 2.0, integrating CTEM principles doesn't require starting over. Start by questioning your current approach:
When did you last test whether your crown jewel protections would stop an actual attack path? Do you know which of your exposures matter most to current threat actors? Can you trace a clear line from your governance priorities to your operational validation activities?
For organizations at NIST Tier 2 or 3, CTEM provides the continuous feedback loop needed to progress toward Tier 4's adaptive approach. For those already at Tier 4, CTEM ensures your adaptability responds to actual threat evolution rather than theoretical scenarios.
The frameworks aren't competing, they're complementary. NIST provides the strategic structure and governance foundation every organization needs. CTEM provides the operational discipline to continuously validate that your NIST implementation actually works.
Summary
A NIST aligned CTEM approach transforms framework implementation from documentation exercise to living security practice. It bridges the gap between what you've implemented and what actually protects you. And in an environment where threats evolve faster than annual assessments can capture, that continuous validation isn't optional, it's how modern security teams stay ahead.
Your framework maturity tier matters less than whether your controls work against real attacks. NIST aligned CTEM gives you both structure and proof.
Here I explore further how to operationalize NIST CSF when aligned to CTEM for financial institutions, I believe this switches up traditional frameworks to become even more powerful.
What's your organization's approach to continuous validation within your framework implementation? Have you found ways to operationalize your governance outcomes?
Further Reading
NIST Cybersecurity Framework:
- NIST CSF 2.0 Official Publication - The complete framework including Core Functions, Organizational Profiles, and Implementation Tiers
- NIST CSF Website - Implementation examples, quick start guides, and community profiles
MITRE ATT&CK Framework:
- MITRE ATT&CK - Comprehensive knowledge base of adversary tactics and techniques based on real-world observations
- Getting Started with ATT&CK - Resources for detection, threat intelligence, and red teaming
Risk Management Integration:
- NIST IR 8286 Series - Integrating Cybersecurity and Enterprise Risk Management
- NIST SP 800-37 - Risk Management Framework for Information Systems and Organizations
Additional Context:
- Best Practices for MITRE ATT&CK Mapping - CISA guidance on using ATT&CK for threat analysis
Continuous Threat Exposure Management (CTEM):
- Gartner: Implement a Continuous Threat Exposure Management (CTEM) Program - Original 2022 framework introduction and implementation guidance
- Gartner: How to Manage Cybersecurity Threats, Not Episodes - CTEM's five-step approach and business value
- Gartner: 2024 Strategic Roadmap for Managing Threat Exposure - Updated guidance on CTEM maturity and integration


Member discussion