Linux Basics for Hackers: Essential Commands for Cybersecurity Professionals

Article Content
Over 96% of the world's top 1 million web servers run on Linux (W3Techs). Meanwhile, 100% of the top penetration testing distributions like Kali Linux, Parrot OS, BlackArch are built on Linux foundations. If you're serious about cybersecurity then learning Linux basics for hackers should be a core skill on your list.
Why Security Professionals Choose Linux
The numbers tell the story about Linux's dominance in the security field:
- 96% of the world's top servers run on Unix or Linux systems (W3Techs)
- All major penetration testing distributions are Linux-based (Kali, Parrot, BlackArch)
- Most security tools (Nmap, Metasploit, Wireshark) are designed for Linux first
- Cloud infrastructure predominantly runs on Linux variants (AWS, Azure, GCP)
Understanding Linux isn't just about using tools, it's about understanding the environment you'll be testing, defending, or analyzing. Whether you're conducting penetration tests, analyzing logs, or responding to incidents, Linux command line proficiency is foundational.
Backstory to Learning Linux
For years I dipped in and out of Linux and was not fully comfortable, for the last 10 years it became a necessity and I spent a lot of time in the terminal window testing and running tools, diagnosing issues and these days I can get by and work through most tasks but I still continue to learn new things. Part of the motivation to write this guide is having my very own documentation I can refer back to and continue to update.
Still Need Convincing ?
If you still need convincing then watch David Bomball make a compelling case in this introductory tutorial, someone you should definitely be following. Use the rest of this guide as a reference and try out some of the commands for yourself.
Before You Begin
I always find it useful to learn when applying knowledge to a real world task, take a look at running a docker container on a linux host machine like ubuntu.
Essential File System Navigation
Security work requires rapid navigation through complex directory structures. You'll be hunting for configuration files, analyzing logs, and examining system artifacts constantly.
Critical Directories for Security Work
- /var/log/ - System and application logs (your goldmine for incident response)
- /etc/ - Configuration files (where misconfigurations hide)
- /tmp/ - Temporary files (where attackers often stage payloads)
- /home/ - User directories (where sensitive data lives)
- /proc/ - Process information (real-time system status)
Below you can see a typical directory structure including the root directory.

Must-Know Navigation Commands
Basic Movement:
pwd- Print working directory (always know where you are)cd- Change directory (cd -returns to previous location, essential for quick pivots)ls -la- List files with hidden items and permissions (the-laflags are critical)
Quick Search:
find / -name "*.conf"- Locate configuration files system-widelocate filename- Fast file search using cached databasewhich command- Find binary locations (verify you're using the intended tool)
Pro tip: Use tab completion constantly. Type first few letters and press TAB - it saves time and prevents typos that could expose your presence during penetration tests.
Understanding Linux Permissions (Security Goldmine)
Permission misconfigurations are among the most common security vulnerabilities. Understanding the permission model is crucial for both offense and defense.
The Permission Model
Linux uses a simple but powerful permission system:
- Owner (u) - File creator/owner
- Group (g) - Users in the same group
- Others (o) - Everyone else
Each category has three possible permissions:
- Read (r/4) - View file contents
- Write (w/2) - Modify file
- Execute (x/1) - Run as program
Security-Focused Permission Commands
Viewing Permissions:
ls -l- See permissions in symbolic format (rwxr-xr-x)stat filename- Detailed file information including timestamps
Modifying Permissions (for testing):
chmod 644 file- Standard file permissions (owner: rw-, group: r--, others: r--)chmod +x script.sh- Make script executablechown user:group file- Change file ownership
Finding Permission Issues:
find / -perm -4000- Find SUID binaries (privilege escalation goldmine)find / -writable -type d- Find world-writable directories (security risk)find /home -type f -perm 0777- Find files with overly permissive settings
Process Management for Security Analysis
Monitoring and manipulating processes is essential for threat hunting, incident response, and understanding system behavior.
Core Process Commands
| Command | Security Use Case | Example |
|---|---|---|
| ps aux | View all running processes with user and resource info | ps aux | grep ssh |
| top / htop | Real-time process monitoring (detect resource-hungry malware) | htop (interactive) |
| netstat -tulpn | Show listening ports and established connections | netstat -tulpn | grep LISTEN |
| ss -tunap | Modern replacement for netstat (faster, more detailed) | ss -tunap |
| lsof -i | List open files and network connections (find what's connected) | lsof -i :443 |
| kill / killall | Terminate processes (IR response to active threats) | kill -9 [PID] |
Note: ss is the modern replacement for netstat and should be your default choice for socket statistics on newer systems.
Text Processing for Log Analysis
Security professionals spend significant time analyzing logs. Mastering text processing commands transforms hours of manual work into seconds.
The Power Trio: grep, sed, awk
grep - Search and Filter
grep "Failed password" /var/log/auth.log- Find failed login attemptsgrep -r "password" /etc/- Recursively search configuration filesgrep -v "success" logfile- Invert match (show everything except success)
sed - Stream Editor (find and replace)
sed 's/old/new/g' file- Replace text in filessed -n '100,200p' largefile- Print specific line ranges
awk - Pattern Scanning (data extraction)
awk '{print $1}' access.log- Extract first column (IP addresses)awk '/404/ {print $1, $7}' access.log- Find 404 errors with IPs and paths
Practical Log Analysis Examples
Find Top IP Addresses in Access Logs:
cat access.log | awk '{print $1}' | sort | uniq -c | sort -rn | head -10
Extract Failed SSH Login Attempts:
grep "Failed password" /var/log/auth.log | awk '{print $11}' | sort | uniq -c
Network Reconnaissance Basics
Understanding network commands is fundamental for both offensive security testing and defensive monitoring.
Quick Network Information
System Network Details:
ip addr/ifconfig- Show network interfaces and IP addressesip route- Display routing tablehostname -I- Show all IP addresses for the host
DNS and Web Requests (High-Level Overview):
- dig - DNS lookup tool (we'll dive deep into this in a future guide on DNS reconnaissance)
- curl - Transfer data from URLs (essential for API testing and web reconnaissance, deserves its own detailed article)
- wget - Download files from web (useful for payload staging)
These tools are so powerful they deserve dedicated deep-dives. For now, know that dig is your DNS swiss-army knife and curl is your web interaction workhorse.
Basic Connectivity Testing
ping target.com- Test basic connectivity (ICMP)traceroute target.com- Map the path packets takenc -zv target.com 80-443- Port scanning with netcat
There is tool that can take this to a whole other level, take a look at network scanning with nmap.
User and Group Management
Understanding user contexts is critical for both privilege escalation attacks and proper access control defense.
Key User Commands
whoami- Current userid- User ID and group membershipssudo -l- List sudo privileges (first thing to check in privilege escalation)cat /etc/passwd- User account informationcat /etc/shadow- Hashed passwords (requires root)last- Recent login historyw/who- Currently logged-in users
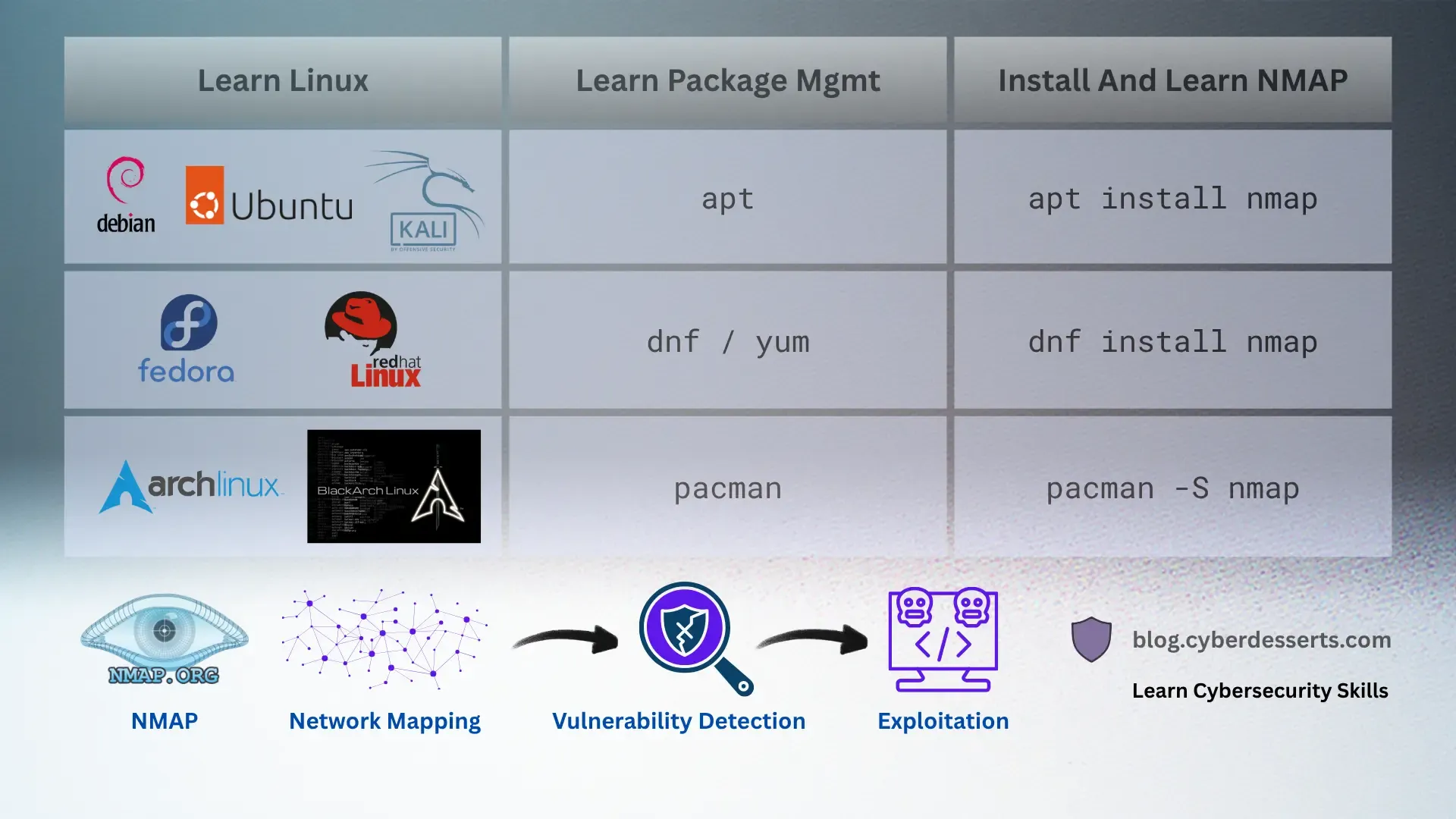
Package Management for Tool Installation
You'll constantly be installing and updating security tools. Each distribution has its own package manager.
Major Package Managers
| Distribution | Package Manager | Common Commands |
|---|---|---|
| Debian/Ubuntu/Kali | apt | apt update && apt upgradeapt install nmap |
| Red Hat/Fedora/CentOS | dnf/yum | dnf updatednf install wireshark |
| Arch/BlackArch | pacman | pacman -Syupacman -S metasploit |
Getting Hands-On: Your First Security Lab
The best way to learn is by doing. Set up a safe practice environment where you can experiment without consequences.
Recommended Setup
Option 1: Virtual Machines (Recommended for Beginners)
- Download VirtualBox or VMware Workstation Player (free)
- Install Kali Linux as a VM (comes with 600+ pre-installed security tools)
- Create a second VM with a vulnerable system (Metasploitable, DVWA)
Here is how you can get started with setting up your own security practice lab
Option 2: Cloud-Based Practice
- TryHackMe or HackTheBox (guided learning paths)
- AWS/Azure free tier for Linux practice
- Docker containers for isolated tool testing
Safety First:
- Never practice attacks on systems you don't own or have explicit permission to test
- Use isolated virtual networks for your lab
- Keep your host system separate from testing environments
Next Steps in Your Linux Security Journey
Mastering these basics gives you the foundation, but security-specific tools take your skills to the next level:
- Network Scanning - Nmap for host discovery and port scanning
- Packet Analysis - Wireshark for network traffic inspection (upcoming guide)
- Exploitation Frameworks - Metasploit for penetration testing (upcoming guide)
- Web Application Testing - Burp Suite, curl, and web-specific tools (upcoming guide)
Subscribe to the blog to get notified when these deep-dive guides are published.
The Bottom Line
Linux command line proficiency isn't just a nice-to-have skill for cybersecurity professionals it's the foundation everything else builds on. With 96% of top servers running Linux and every major security distribution built on Linux foundations, avoiding the command line means limiting your career ceiling.
These essential commands, file navigation, permission analysis, process monitoring, and text processing form the toolkit you'll use daily whether you're hunting threats, testing defenses, or responding to incidents.
Key Resources
- Linux Journey - Interactive Linux learning platform
- OverTheWire Wargames - Practice Linux security challenges
- Kali Linux Documentation - Official pentesting distribution docs
- Explain Shell - Decode complex command syntax
References
- W3Techs (2024). "Usage Statistics of Unix for Websites." Web server technology survey data.
- Kali Linux Project. "About Kali Linux." Official distribution documentation on security-focused Linux architecture.
- TryHackMe. "Linux Fundamentals." Educational platform statistics on cybersecurity skill development.
Next in Series: Network Scanning with Nmap - From Host Discovery to Vulnerability Detection




Member discussion