AI Browser Security Risks: What to Know
Gartner just told enterprises to block all AI browsers (Gartner, December 2025). The advisory arrives as 27.7% of organisations
Cloud Security Fundamentals: What Every Organization Needs to Know
Ninety-four percent of enterprises now use cloud services, yet cloud misconfigurations remain the leading cause of data breaches. If your
Cybersecurity Career Playbook - 2026
18 CYBERSECURITY SKILLS THAT SEPARATE TOP PERFORMERS
AI and Cybersecurity: Some Interesting Thoughts from a Recent Podcast Chat
TL;DR: Attackers build unrestricted AI models while defenders work within ethical guardrails, creating a dangerous asymmetry. Your expertise determines how much AI amplifies your productivity. And sometimes the most sophisticated AI systems still fail because of a default password.
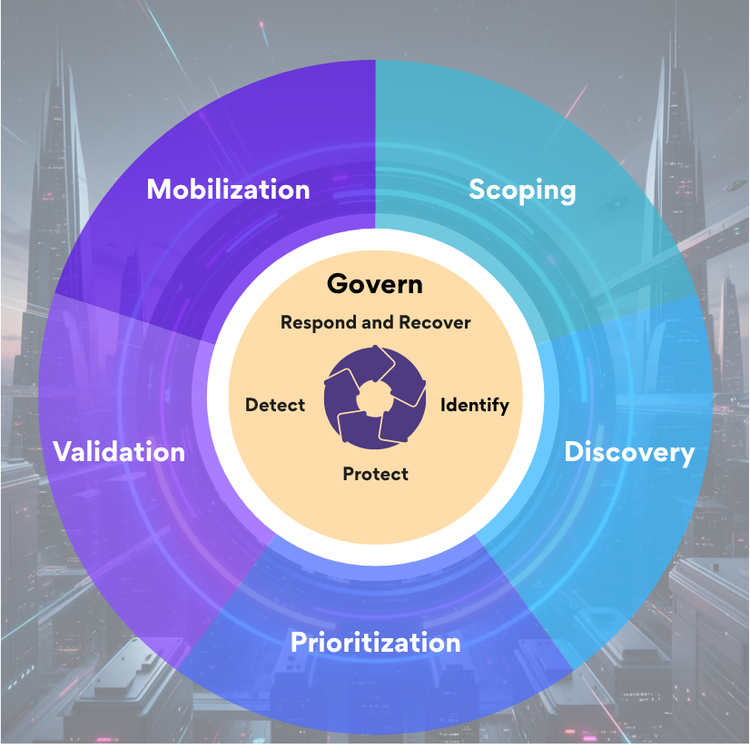
Why NIST Aligned CTEM Is the Framework Integration Security Teams Actually Need
TL;DR - Discover how NIST aligned CTEM transforms framework compliance into operational security. Bridge governance maturity and real threat detection through continuous validation of NIST CSF 2.0 controls.
Writing An Acceptable Use Policy For AI - And What to Put In It
TL;DR: Only 10% of companies have a comprehensive AI policy in place (Security Magazine). Where do you start with writing an acceptable use policy for ai ?
The Shadow AI Crisis: And What You Can Do
This 5-minute check pinpoints your biggest gaps and shows you exactly where to focus for maximum impact.
ELK Stack Security Monitoring Tutorial: Linux, Windows & macOS
Build an ELK stack security monitoring system with Docker in 45 minutes. Learn to deploy Elasticsearch, Logstash, and Kibana for real-time threat detection, tracking authentication failures, network activity, and suspicious behaviour.
Build an npm Vulnerability Scanner (Free deps.dev)
How I created a custom npm vulnerability scanner using deps.dev API to track dependencies and vulnerabilities beyond traditional tools
Choosing A SIEM Platform: Which Is The Most Effective For You ?
Choosing a SIEM? See what security professionals actually use or try them out and share your experience.